GitHub
Track and resolve bugs faster by using data from your GitHub commits, and streamline your triaging process by creating a GitHub issue directly from Sentry.
If you're not sure which GitHub integration you need to configure, please take a look at the URL. URLs like https://github.com/org-name are usually for GitHub-hosted accounts and should use the regular GitHub (not GitHub Enterprise) integration. See Install for more details.
Self-hosted GitHub Enterprise accounts typically have URLs that look more like https://github.org-name.com (or some other customization of the domain). In this case, you should configure the GitHub Enterprise integration.
Sentry owner, manager, or admin permissions, and GitHub owner permissions are required to install this integration.
Navigate to Settings > Integrations > GitHub.
If you have the legacy GitHub integration installed, use the button next to GitHub to Upgrade. If you don't have the legacy GitHub integration installed, use the button to Install.
In the resulting modal, click "Add Installation".
A GitHub install window should pop up. Click "Install".
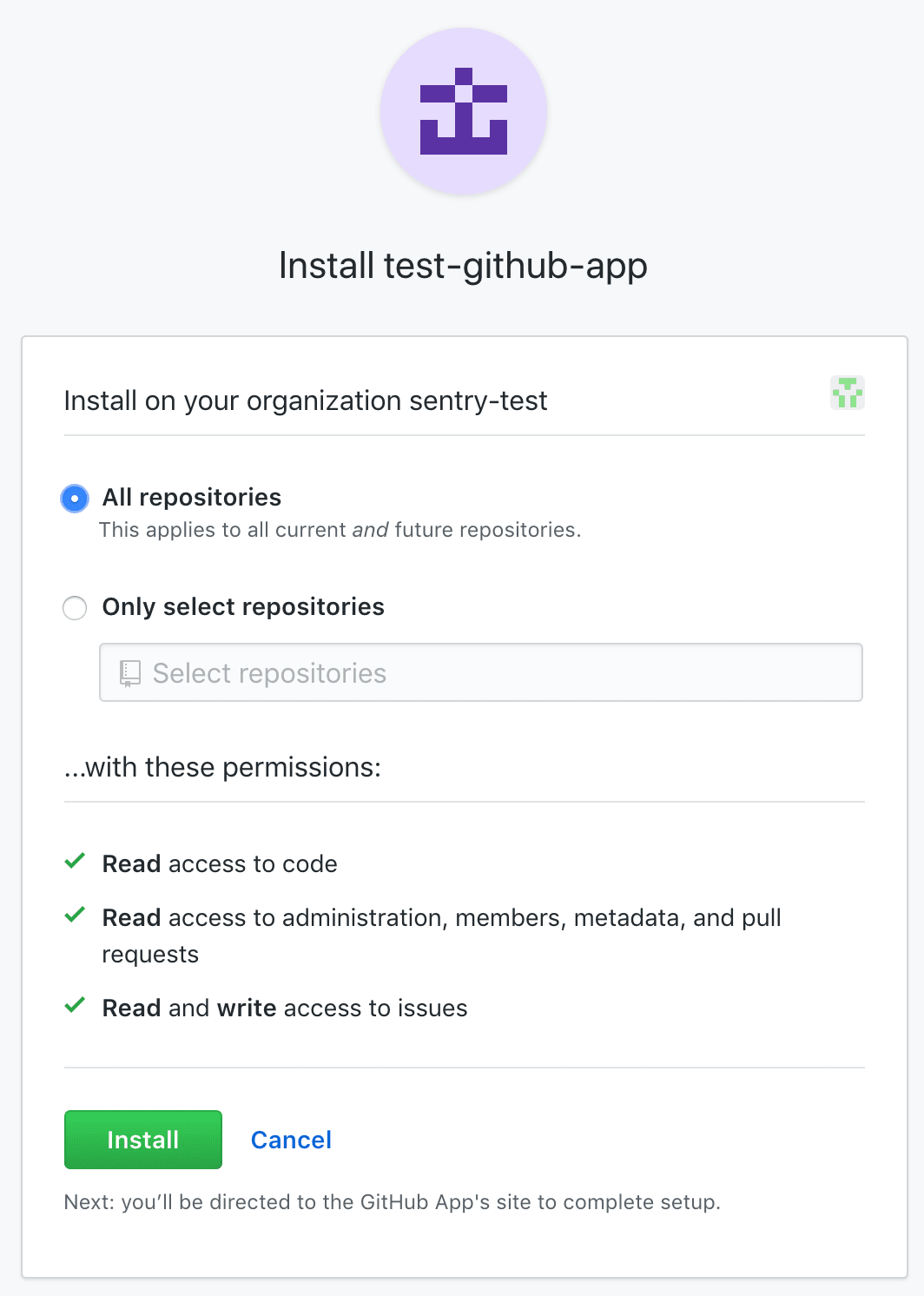
Select which repositories Sentry should have access to (or select all repositories).
You should then be redirected back to the Sentry Integrations page.
On your new GitHub instance in Sentry, click "Configure".
All of your repositories will be added by default, you just have to refresh your screen. To only add select repositories, choose them from the dropdown list. Make sure you have given Sentry access to these repositories in GitHub in the previous steps.
The GitHub integration is available for all projects under your Sentry organization. You can connect multiple GitHub organizations to one Sentry organization, but you cannot connect a single GitHub organization to multiple Sentry organizations.
If your GitHub Enterprise instance is self-hosted/on-prem, follow the instructions below. If you're using GitHub Enterprise Cloud, follow the instructions for GitHub.
Confirm Sentry's IP ranges are allowed for your GitHub Enterprise instance.
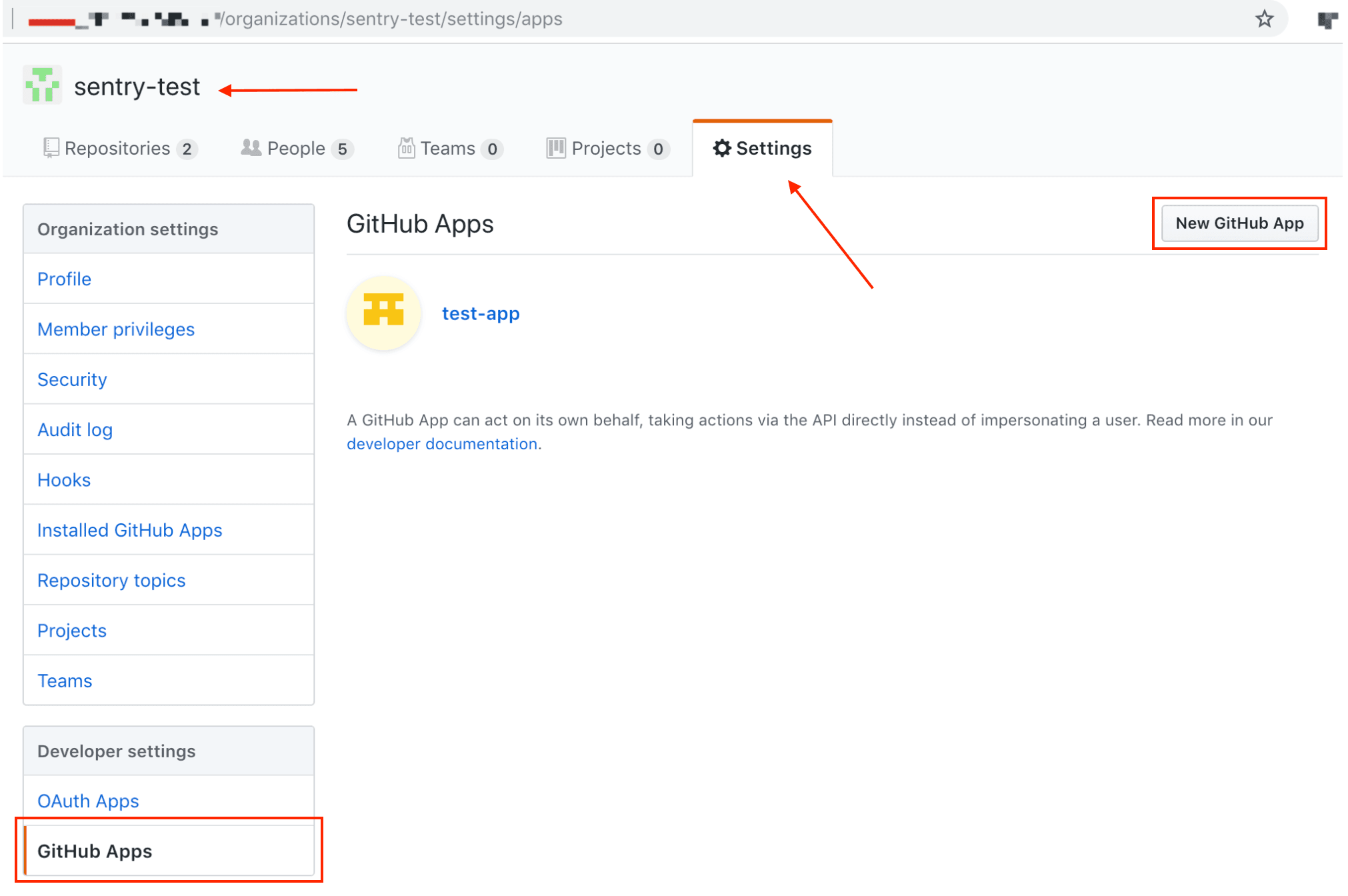
In your GitHub Enterprise organization, navigate to Settings > Developer Settings > GitHub Apps and click to add a new New GitHub App.
First, you'll need to generate a webhook secret. For example, in terminal:
Copiedopenssl rand -base64 500 | tr -dc 'a-zA-Z0-9' | fold -w 64 | head -n 1Then in GitHub, fill out the form as follows and click "Create GitHub App".
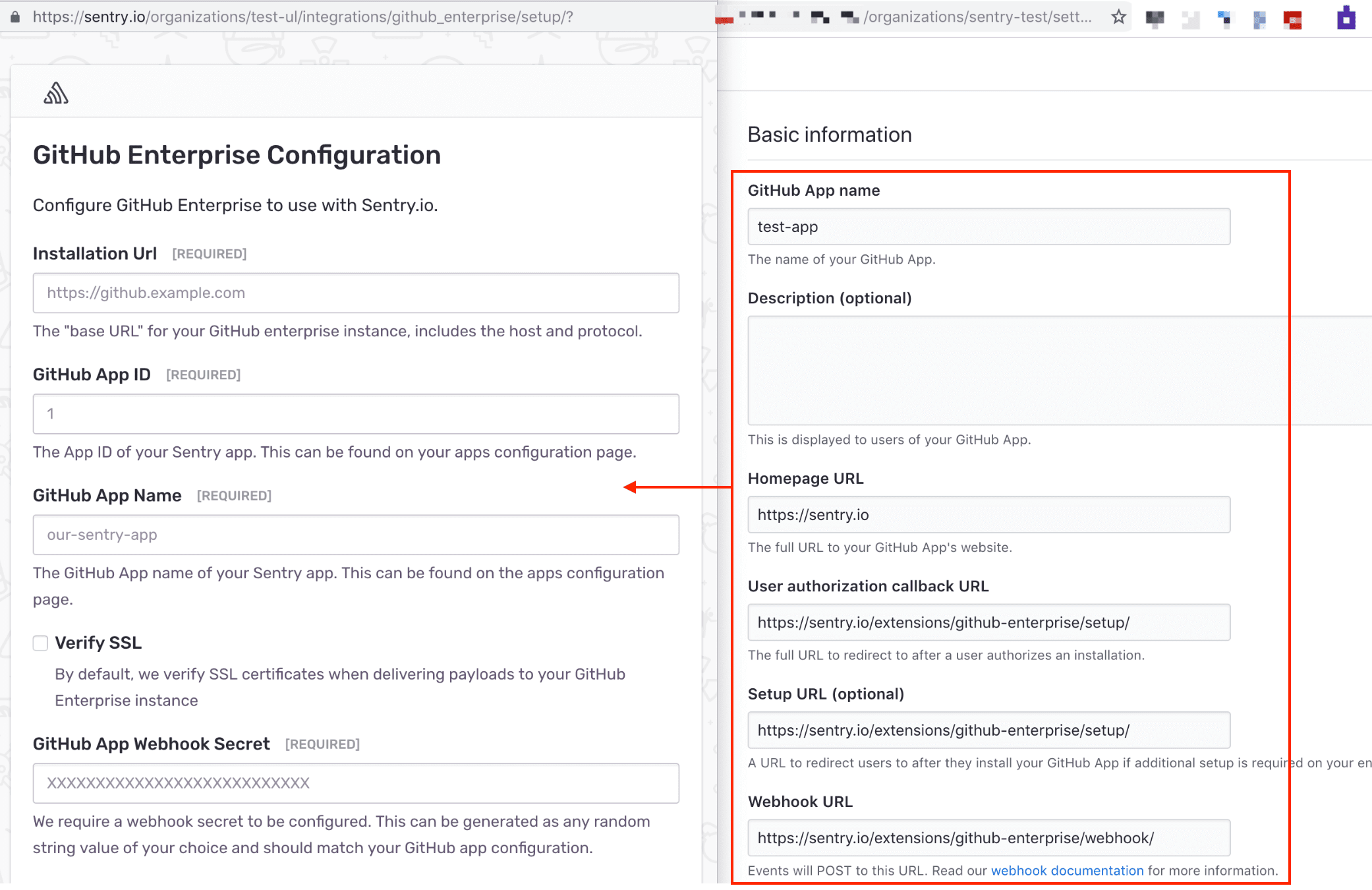
GitHub App Name sentry-app Homepage URL https://sentry.io User authorization callback URL https://sentry.io/extensions/github-enterprise/setup/ Setup URL https://sentry.io/extensions/github-enterprise/setup/ Webhook URL https://sentry.io/extensions/github-enterprise/webhook/ Webhook secret Input your secret from the previous stepRepository Administration Read-only Commit Statuses No Access Deployments No Access Issues Read & Write Pages No Access Pull Requests Read-only Repository Contents Read-only Single File No Access Repository Projects No Access Organization members Read-only Organization projects No Access Subscribe to Events
Pull Request Yes Push Yes
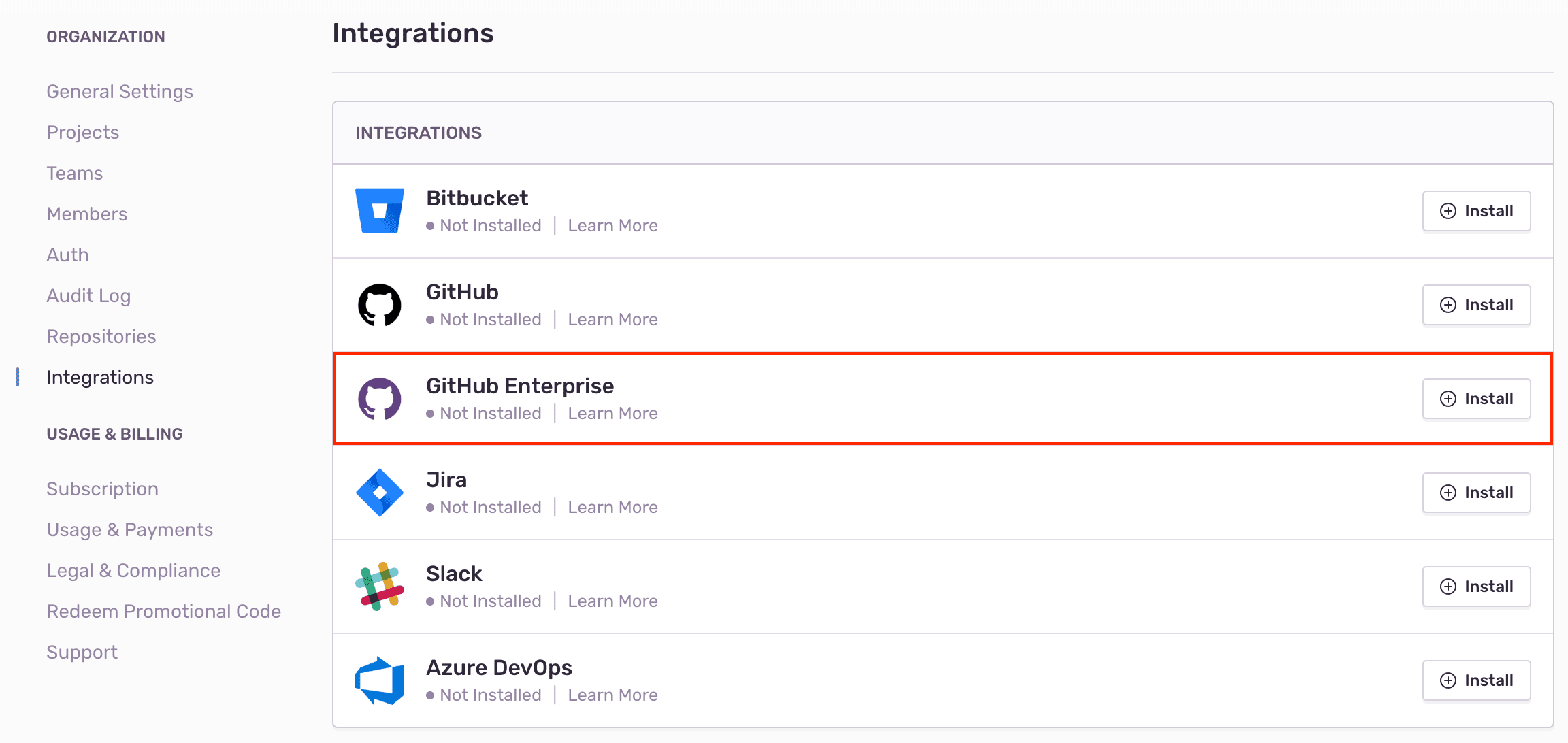
In Sentry, navigate to Organization Settings > Integrations.
Next to GitHub Enterprise, click "Install".
Click "Add Installation".
Fill out the following form with information from your GitHub apps configuration page.
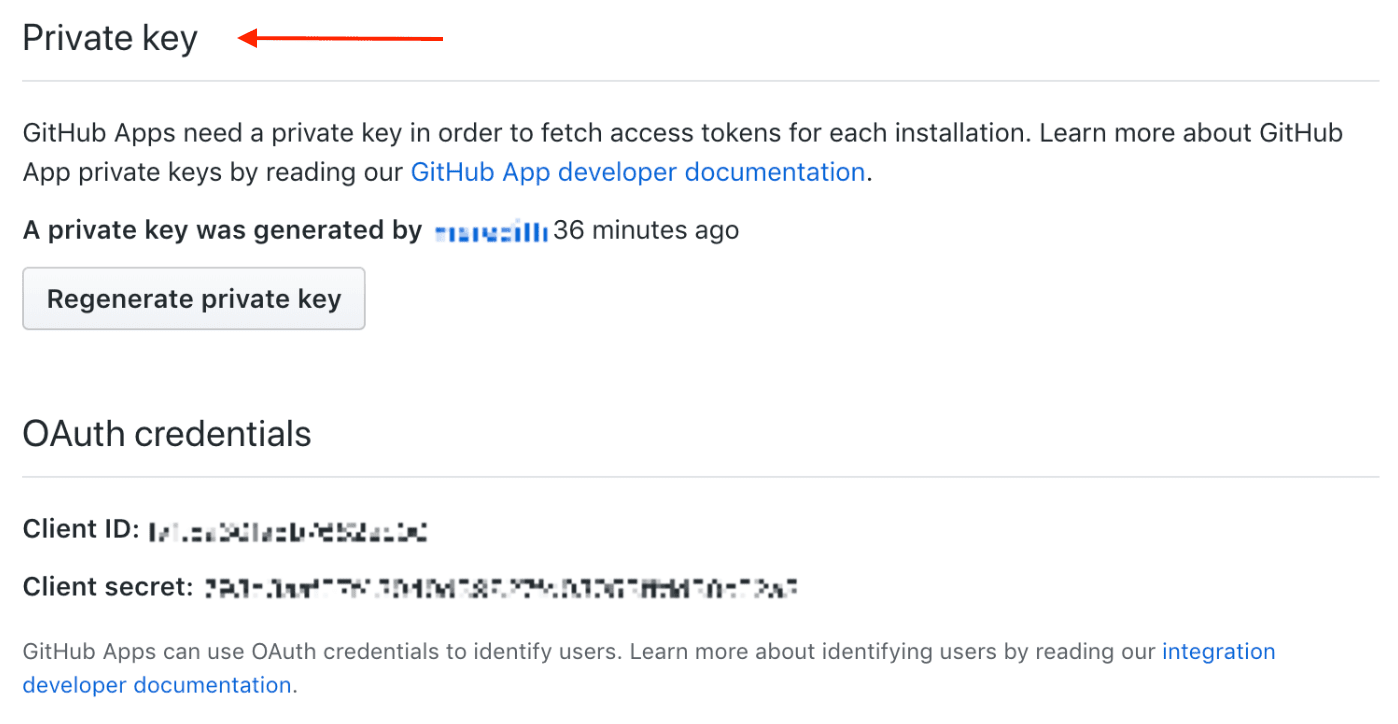
You'll need to generate a private key on your GitHub apps configuration page, and paste the entire contents into the GitHub App Private Key field.
For example, in terminal:
Copiedcat <YOUR_PRIVATE_KEY_FILE> | pbcopyClick "Configure" and then a GitHub install window will pop up. Select which repositories Sentry should have access to (or select all repositories) and click "Install".
You will then be redirected back to Sentry. On your new GitHub Enterprise instance, click "Configure".
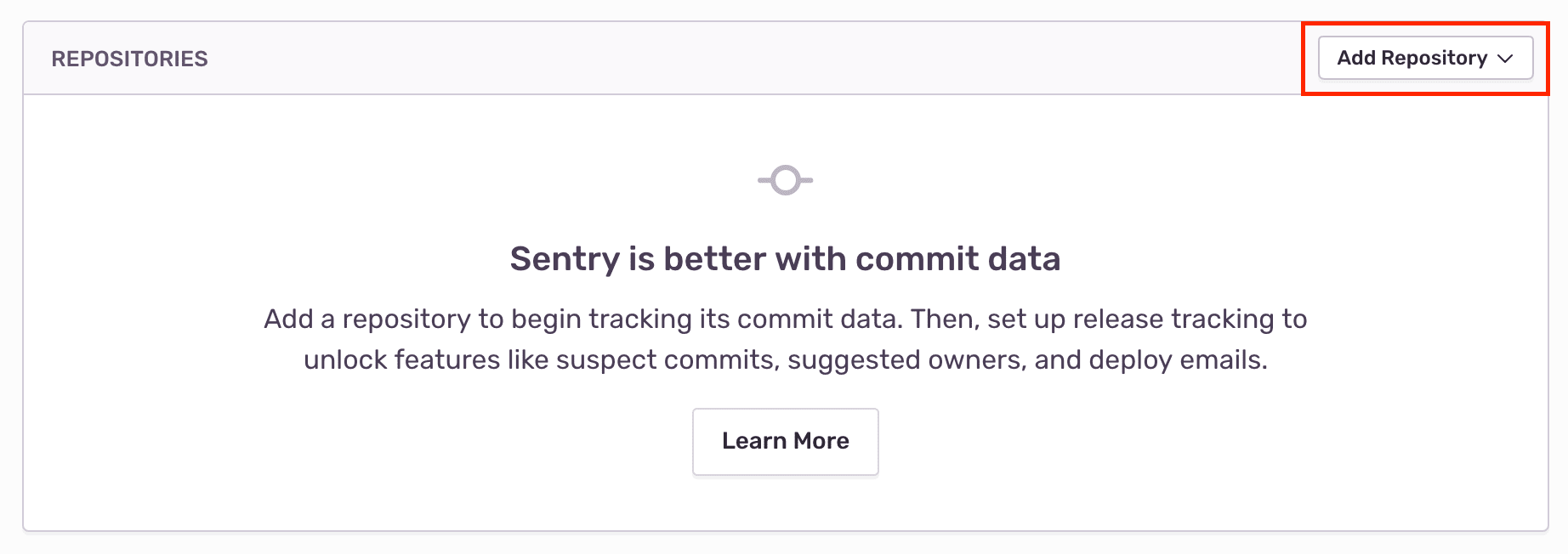
Add any repositories that you want to collect commit data from. Make sure you have given Sentry access to these repositories in GitHub in the previous steps.
GitHub Enterprise should now be enabled for all projects under your Sentry organization.
Use GitHub to track commits, identify suspect commits, resolve via commit or PR and manage issues.
Commit tracking allows you to hone in on problematic commits. Learn more about commit tracking.
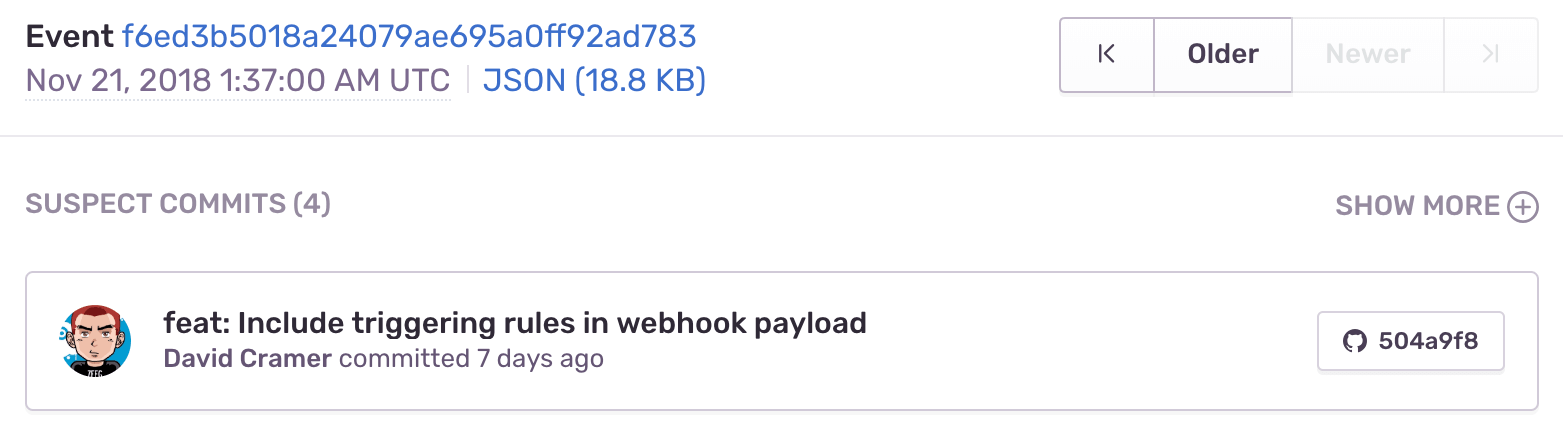
Once you set up commit tracking, you’ll be able to see the most recent changes to files found in the issue’s stack trace with suspect commits.
For issues where the files in the stack trace match files included in commits sent to Sentry, you’ll see the suspect commit, with a link to the commit itself.
You’ll also see that the author of the suspect commit will be listed as a suggested assignee for this issue. To assign the issue to the suggested assignee, click on their icon.
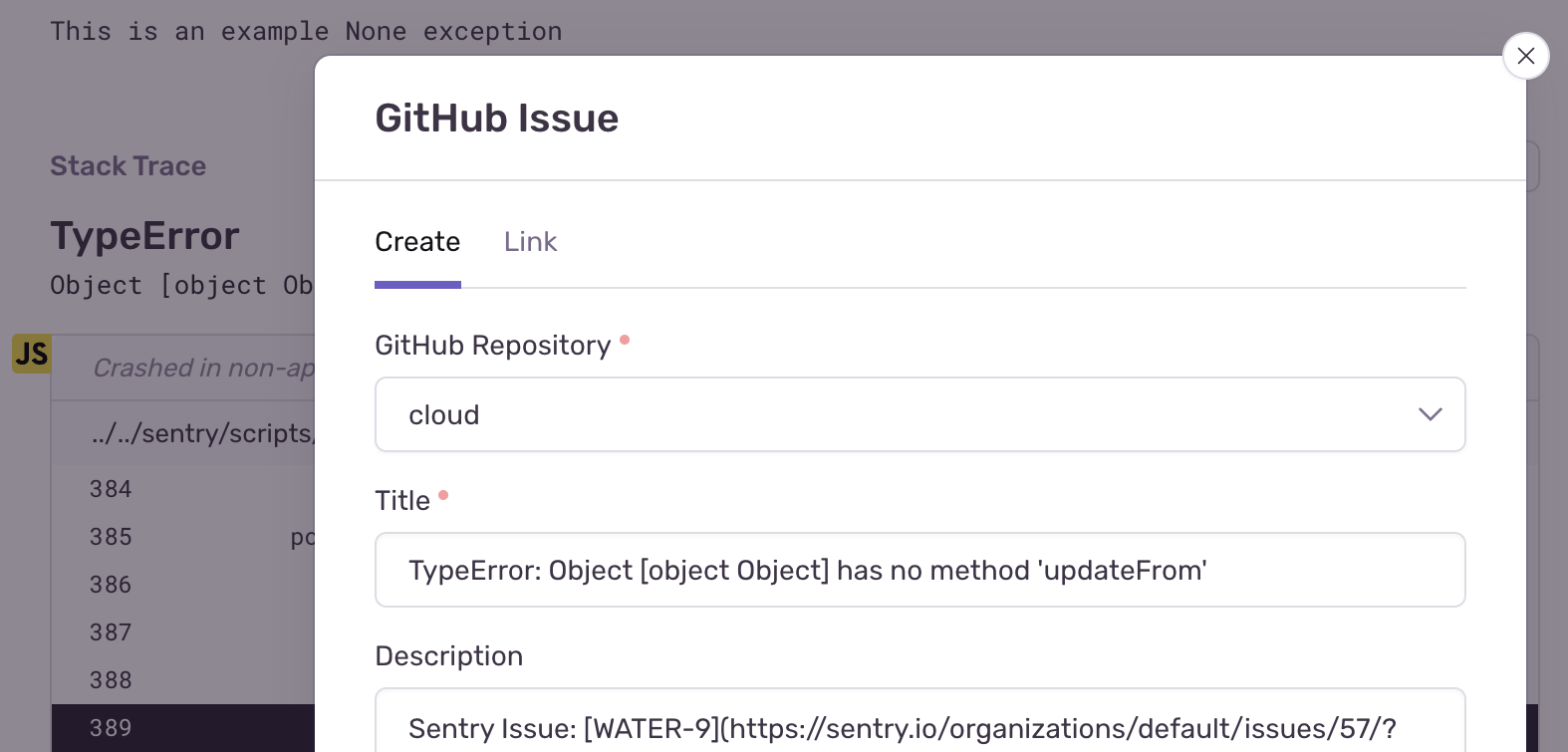
Issue tracking allows you to create GitHub issues from within Sentry, and link Sentry issues to existing GitHub Issues.
Note
Manual issue management is available to organizations on Team, Business, and Enterprise plans.
Automatic issue management is available to organizations that include transactions in their Business and Enterprise plans.
Issue management can be configured in two ways - automatically or manually.
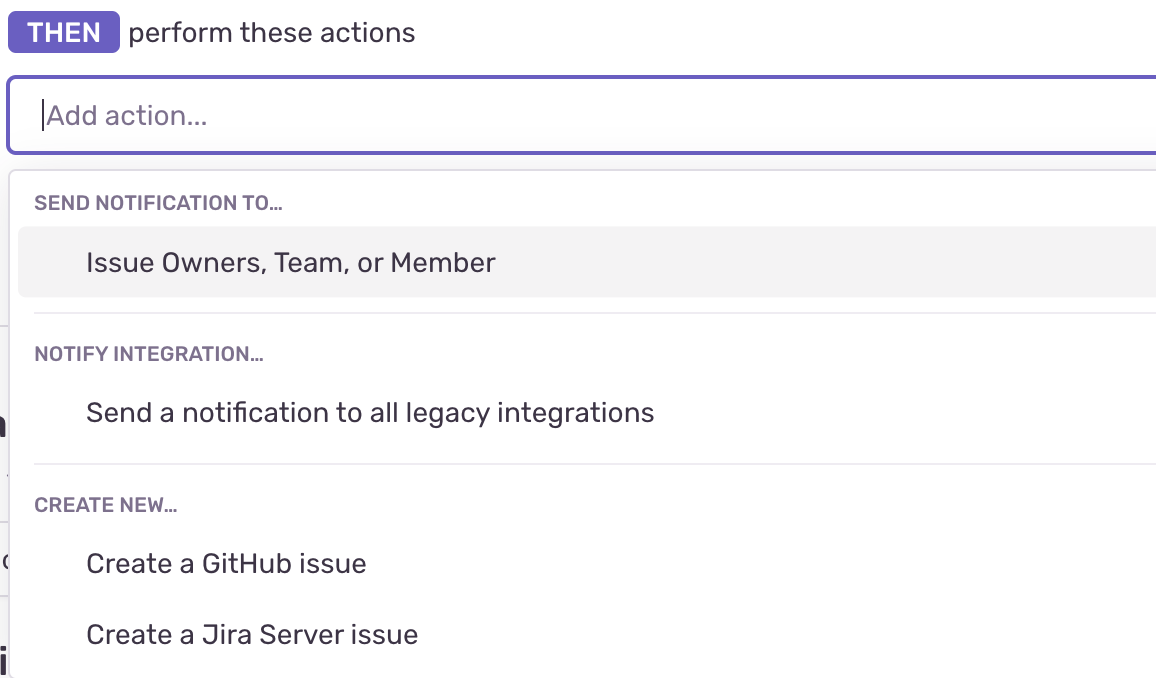
To configure issue management automatically, create an Issue Alert. When selecting the action, choose Create a new GitHub issue.
A GitHub issue will be created automatically when the alert has been triggered.
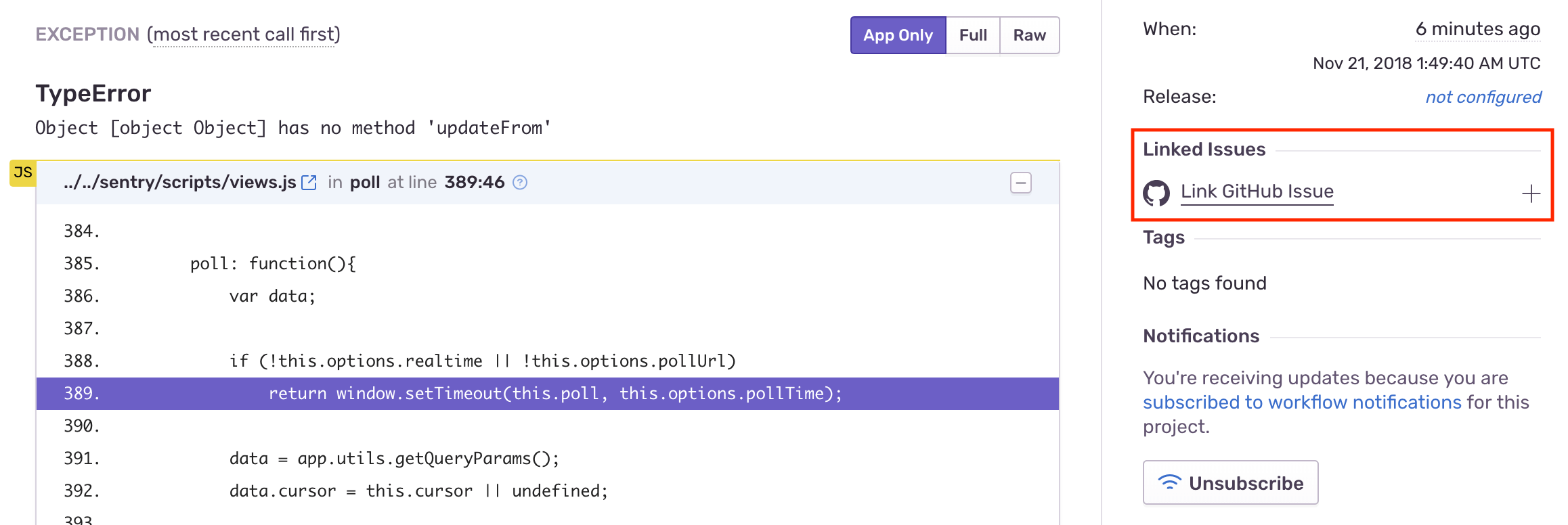
To configure issue management manually, once you've navigated to a specific Sentry issue, you'll find the Linked Issues section on the right hand panel.
Here, you’ll be able to create or link GitHub issues.
Once you are sending commit data, you can start resolving issues by including fixes <SENTRY-SHORT-ID> in your commit messages. For example, a commit message might look like:
Prevent empty queries on users
Fixes MYAPP-317
You can also resolve issues with pull requests by including fixes <SENTRY-SHORT-ID> in the title or description.
When Sentry sees this, we’ll automatically annotate the matching issue with a reference to the commit or pull request, and, later, when that commit or pull request is part of a release, we’ll mark the issue as resolved. The commit must be associated with a release. Otherwise, if the commit is squashed, Sentry won’t know when the commit has been released, and the issue may never be marked as a regression. With GitHub, we recommend using fixes <SENTRY-SHORT-ID> in the body of your pull request that is going to be merged to your main branch.
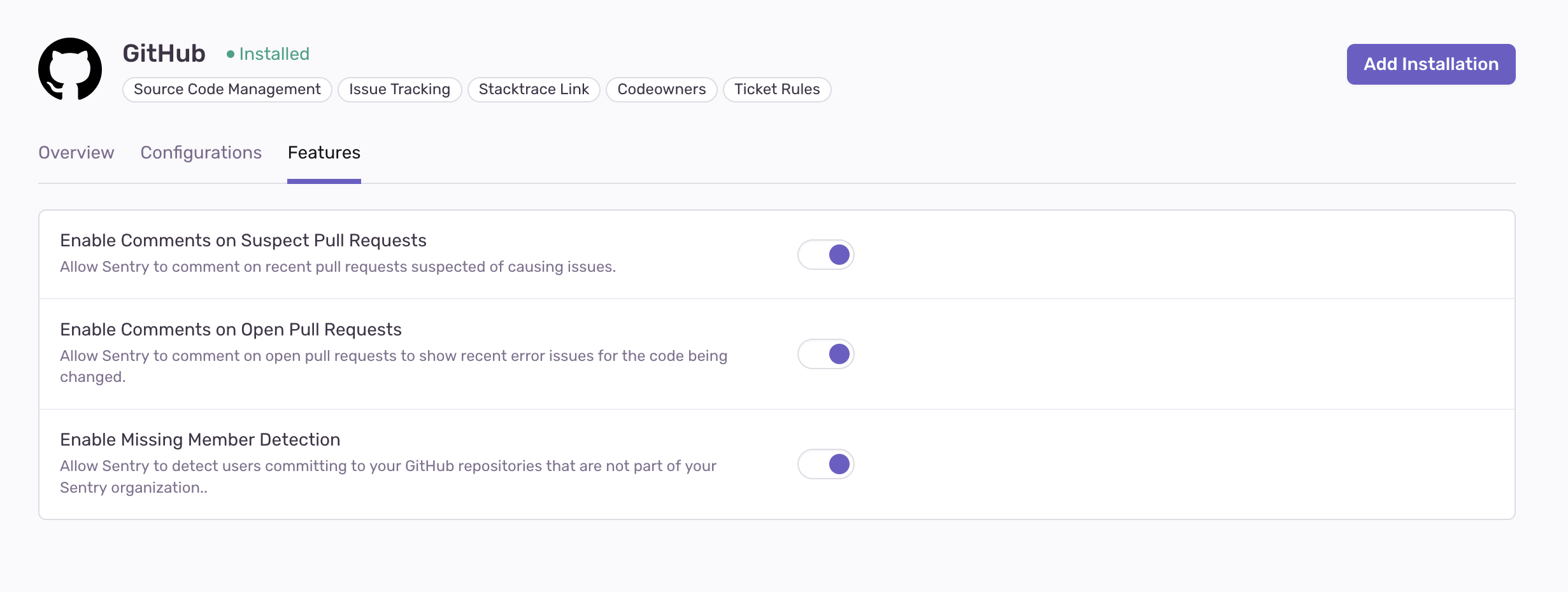
Sentry can comment on merged and open pull requests. These features are automatically enabled once your GitHub integration has been set up. To disable it, go to Settings > Integrations > GitHub and toggle it off.
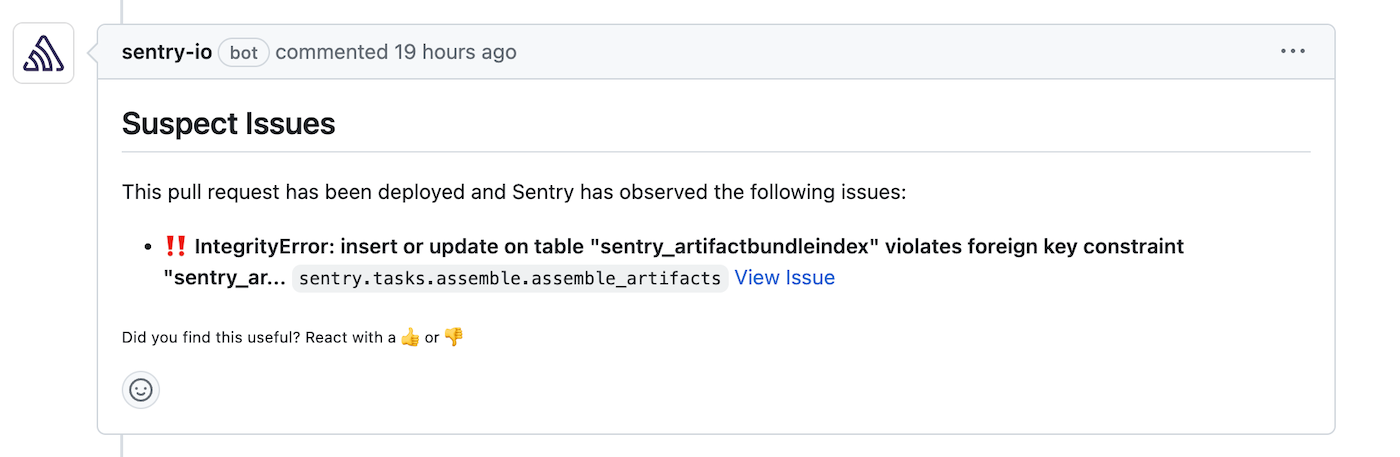
If a recently merged pull request is suspected of causing an issue, Sentry will comment on it to surface the issue, as shown in the example below.
Sentry will only comment on pull requests less than two weeks old that are associated with suspect commits. The comment will continuously be updated with up to five issues the pull request is suspected to have caused.
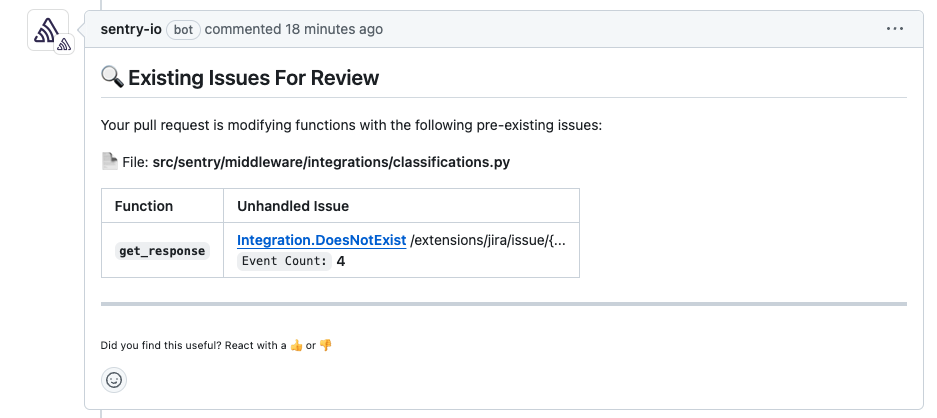
When a pull request is opened, Sentry will parse the filenames and function names modified in the pull request from the PR diff to find recent unhandled, unresolved issues associated with your pull request.
Sentry will comment on the pull request with up to five issues per file that were first seen within the past 90 days and were last seen within the past 14 days.
This feature requires code mappings and is currently only supported for Python, Javascript/Typescript, PHP, and Ruby files. For Javascript/Typescript, please ensure that you've unminified your code by setting up source maps.
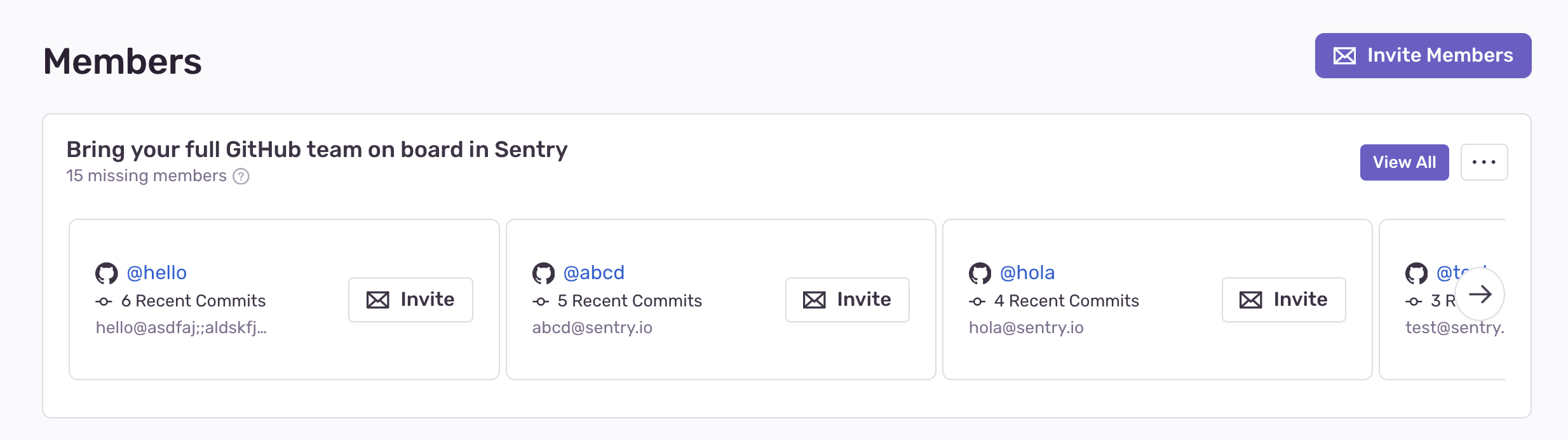
If there are users committing to Github repositories linked to Sentry and they're not members of your organization, Sentry detects them as missing members. Once a month, Sentry sends organization owners and managers an email reminding them to invite those users to join their org. Sentry also shows a banner to invite missing members in the Settings > Members page.
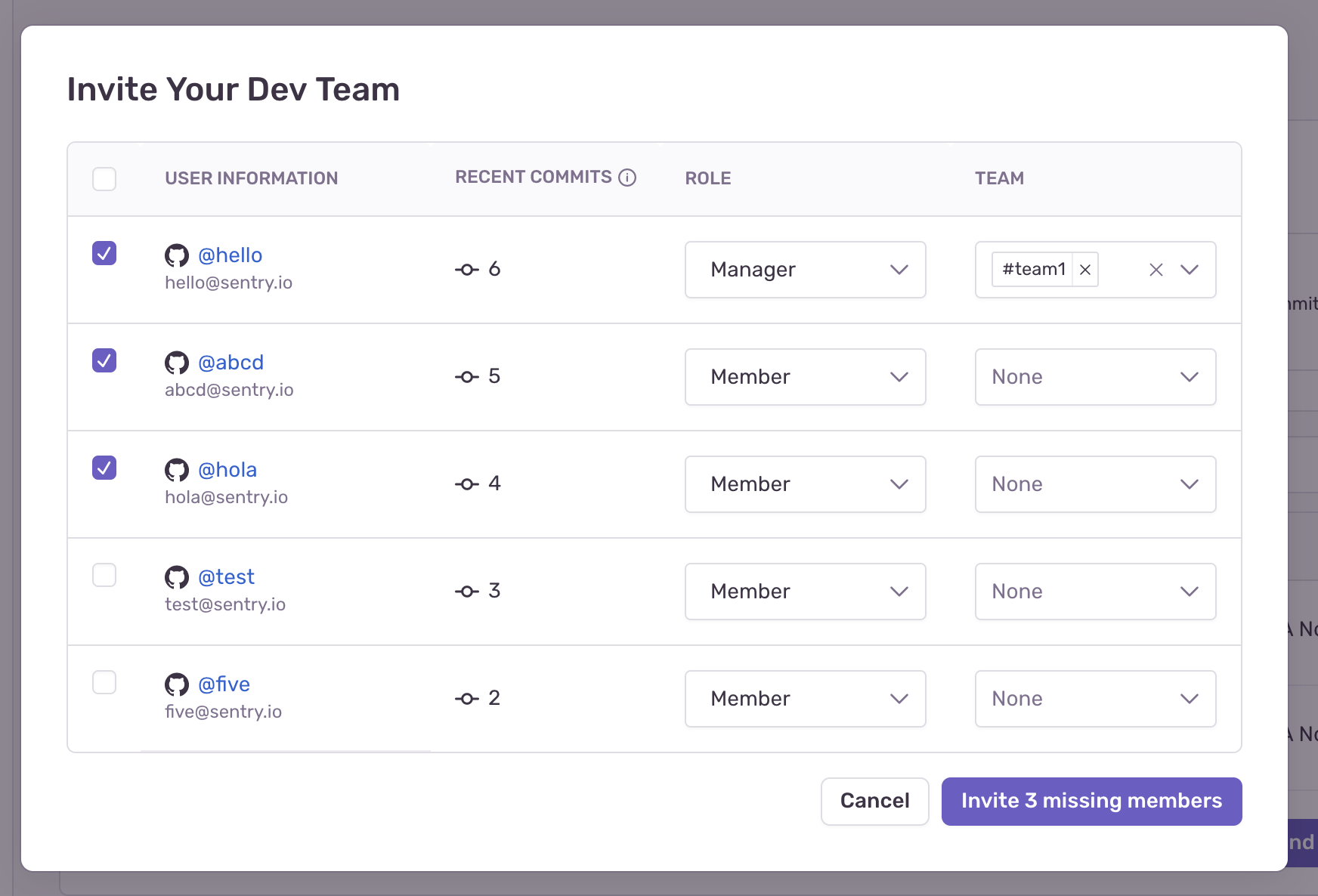
The banner shows the 5 most active contributors that are not yet in the organization. To see all missing members (up to 50), click "View All" in the banner. To snooze the banner, click the ellipsis, then select "Hide Missing Members".
Clicking "View All" on the invite banner will display the invite modal. From here, you can select multiple users and assign roles and teams before inviting them.
By default, this feature is automatically enabled once your GitHub integration has been set up. To disable it, go to Settings > Integrations > GitHub and toggle it off.
Sentry will automatically try to set up code mappings on Python, JavaScript, Node.js, Ruby, PHP, and Go projects for organizations with the GitHub integration installed. If your project uses a different SDK, you can add code mappings manually. Support for other languages and other source code integrations is being worked on.
Stack trace linking takes you from a file in your Sentry stack trace to that same file in your source code. If you have commit tracking set up in Sentry, we can take you to the exact version (using the commit associated with the event) of the source code when the error occurred. Otherwise we'll link you to the current state of the source code (using the default branch).
Navigate to Settings > Integrations > GitHub > Configurations.
Click the "Configure" button next to your GitHub Instance.
Click the Code Mappings tab.
Set up a code mapping for each project for which you want to enable stack trace linking. To create a new code mapping, click Add Mapping.
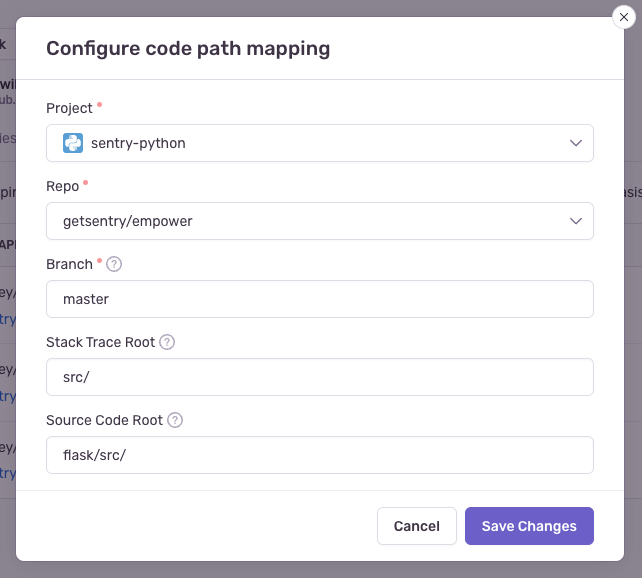
Fill out the form, then click Save Changes. Each form field is described below:
- Project (required): This is the Sentry project.
- Repo (required): This is the GitHub repository associated with the Sentry project above. If you have more than one GitHub repository being used per Sentry project, you'll need multiple code mappings.
- Branch (required): This is the default branch of your code we fall back to if you do not have commit tracking set up.
- Stack Trace Root and Source Code Root (optional): See below for information on determining these values.
The following information is only valid for platforms which use traditional file paths. Platforms with package names require additional steps. For Java, read more in the page on source context.
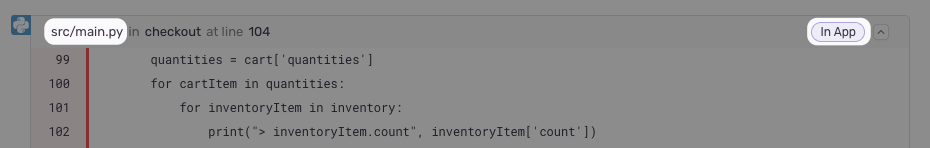
First, navigate to a stack trace that you wish to map. Find an In App frame, which is denoted by a bubble on the right side of the frame. The filename will be shown as the first piece of text at the left hand side of the frame header. In this example, it is src/main.py.
For certain native platforms, the stack trace will look different. In cases like these, you can find the absolute path by hovering over the filename.
If you aren’t sure, you can look at the event JSON by clicking on the {} button in the event header. Find the text in the frame's filename or abs_path.
Next, locate the file seen in the stack trace with your source code provider (e.g. GitHub). In this example, the path is flask/src/main.py (empower is ignored since it is the name of the repo).
Compare the file path from the stack trace with the path found in your source repository. In this example, the src/ folder in the stack trace matches the flask/src folder in the source code. Using that information, set the Stack Trace Root to src/ and the Source Code Root to flask/src/. This tells Sentry to replace all file paths beginning in src/ with flask/src/ when searching for the source code.
For best results, we recommend always providing a non-empty value for the Stack Trace Root when possible.
This feature is available only if your organization is on a Business or Enterprise plan.
Import your existing GitHub CODEOWNERS files to automatically assign Sentry issues and route alerts to the responsible individuals and teams.
For more details, see the full documentation for Code Owners.
Single sign-on (or SSO) allows you to manage your organization’s entire membership via a third-party provider.
For more details, see the full documentation for Single Sign-on.
If you’re having issues adding a GitHub repository:
- Make sure you are the Owner of your GitHub organization.
- Disconnect, and then reconnect your GitHub Identity.
If you're having trouble setting up Sentry with your on-premises integration, verify the following:
- The provided installation URL is a fully qualified domain name (FQDN), which is resolvable on the internet.
- The IP addresses Sentry uses to make outbound requests are allowed.
- Sentry's access to your installation URL is not path restricted.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) or suggesting an update ("yeah, this would be better").