Splunk (Legacy)
Learn more about Sentry's Splunk integration, which allows you to send Sentry events to Splunk.
Splunk integration is deprecated and is not availble to be installed on new projects.
Connect Splunk to Sentry with the Data Forwarding feature.
We only support Splunk Cloud plans. We do not support Splunk Enterprise plans. See the Splunk documentation for specific details on your Splunk installation.
This integration needs to be set up in each project for which you wish to use it. It is maintained and supported by the Sentry community.
Sentry owner, manager, or admin permissions are required to install this integration.
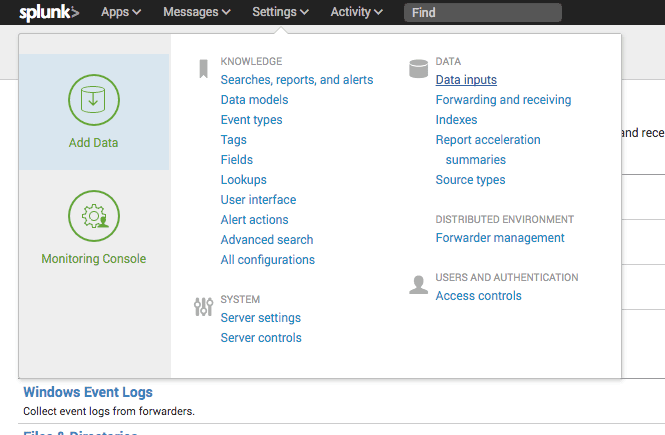
Navigate to Settings > Integrations > Splunk
To get started, you’ll need to first enable the HTTP Event Collector:
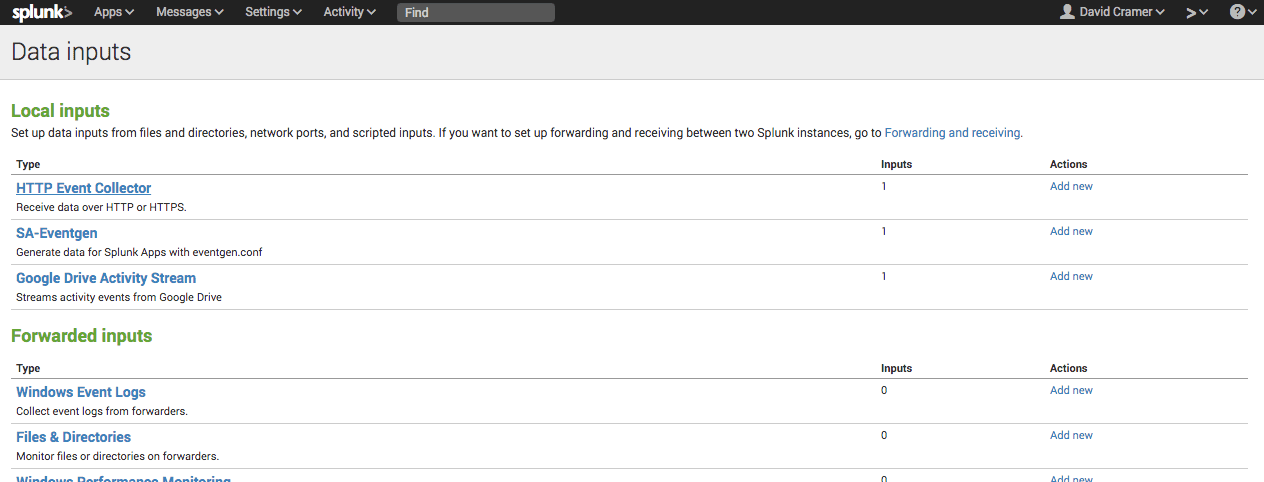
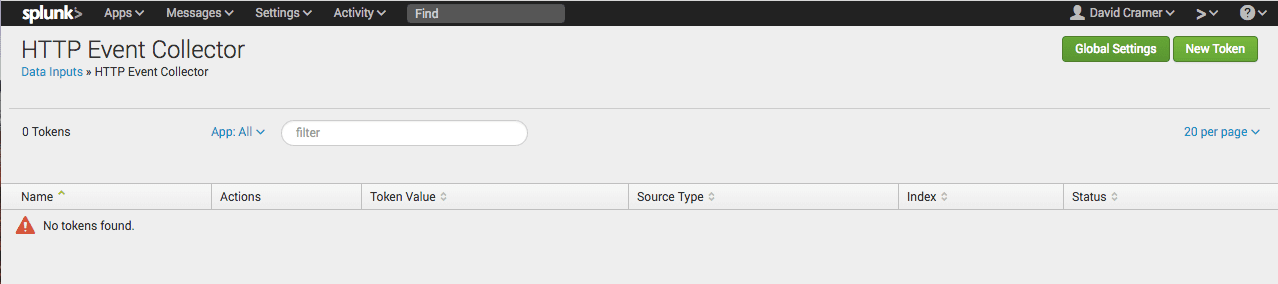
Under Settings, select Data Inputs:
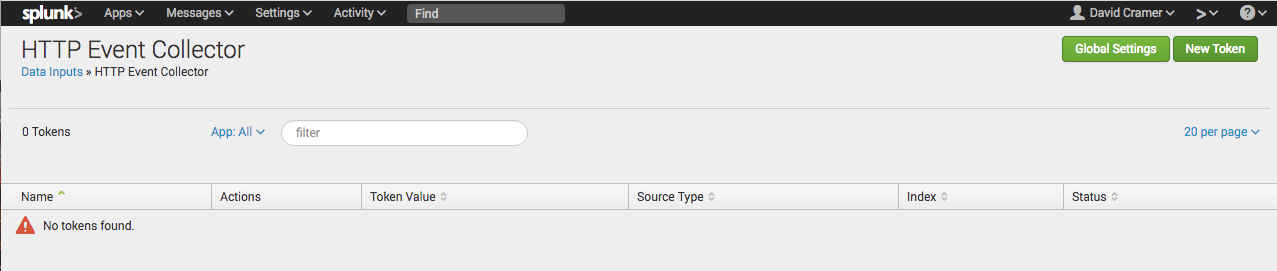
Select HTTP Event Collector under Local Inputs:
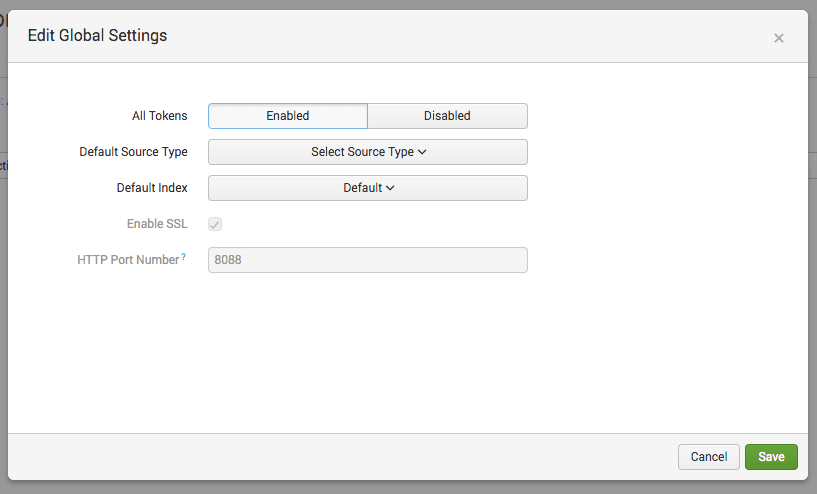
Under your HEC settings, click "Global Settings":
Change All Tokens to Enabled, and note the HTTP Port Number (8088 by default):
If you’re running Splunk in a privileged environment, you may need to expose the HEC port.
Under HTTP Event Collector, create a new Sentry input by clicking "New Token":
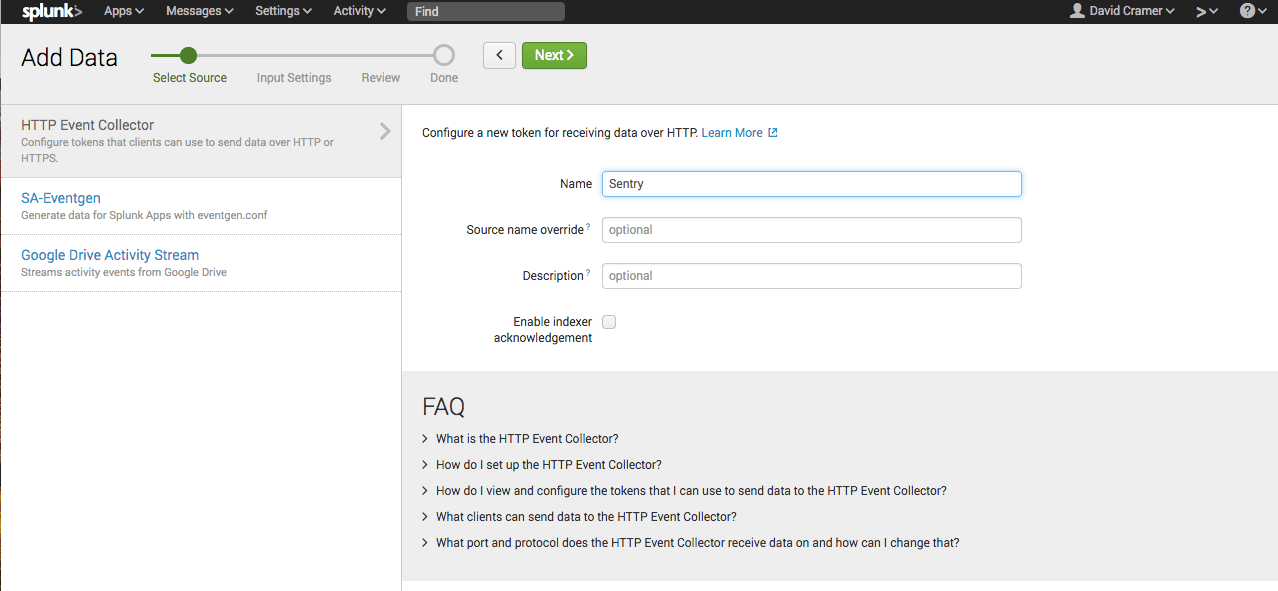
Enter a name (e.g. Sentry), and click "Next":
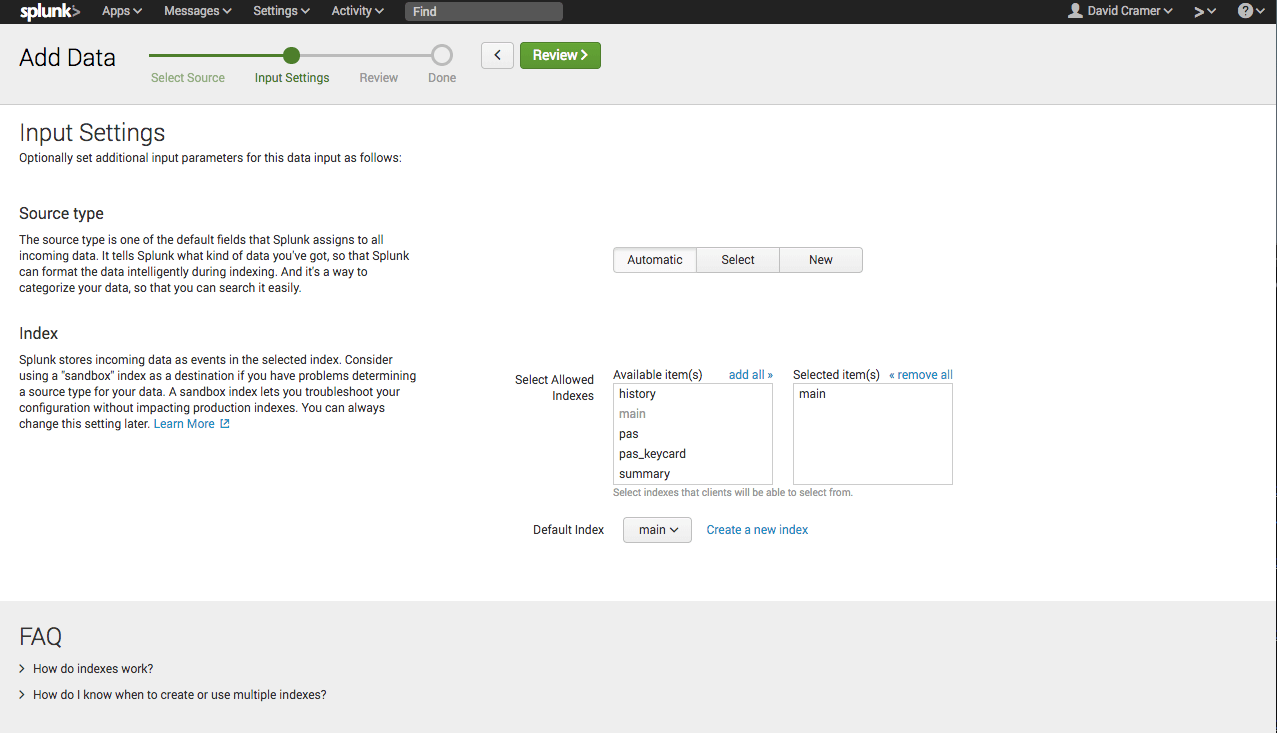
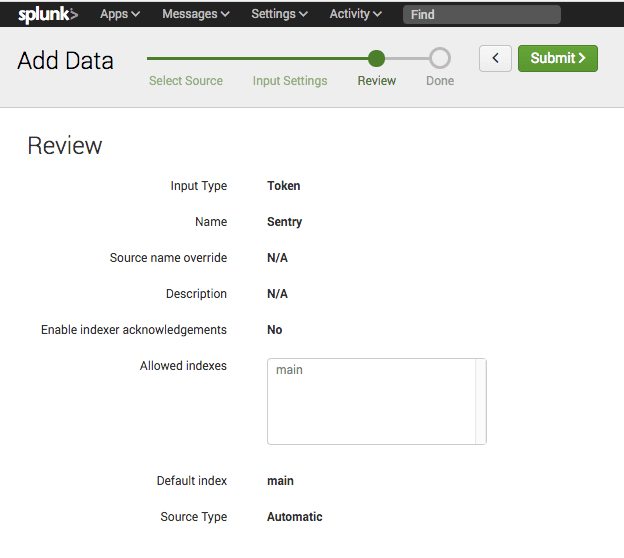
Select the index you wish to make accessible (e.g. main), and click "Review":
You’ll be prompted to review the input details. Click "Submit" to continue:
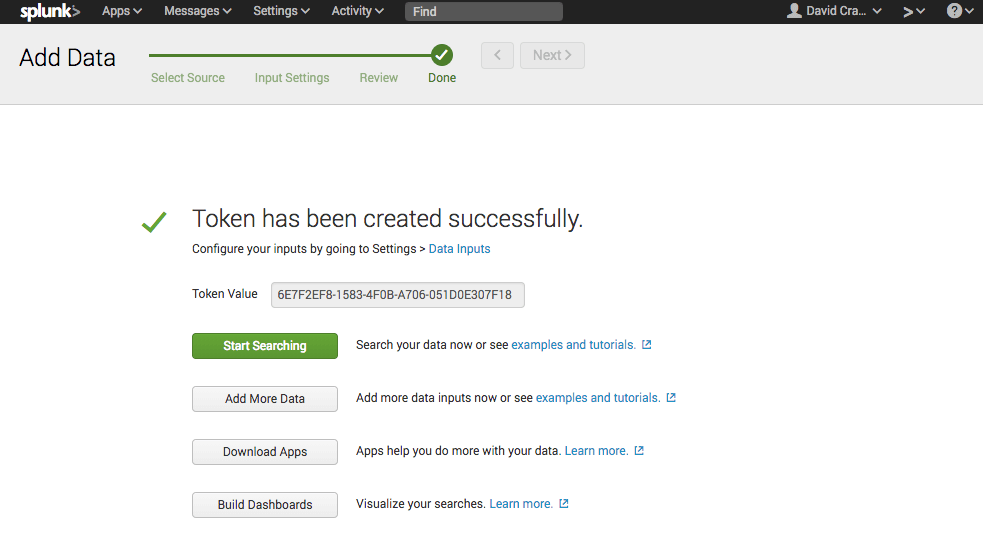
The input has now been created, and you should be presented with the Token Value:
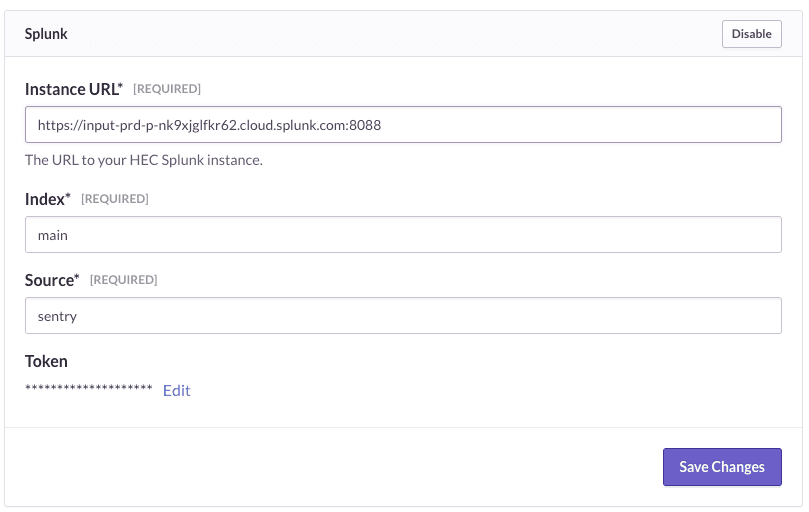
To enable Splunk forwarding, you’ll need the following:
- Your instance URL (see note below)
- The Sentry HEC token value
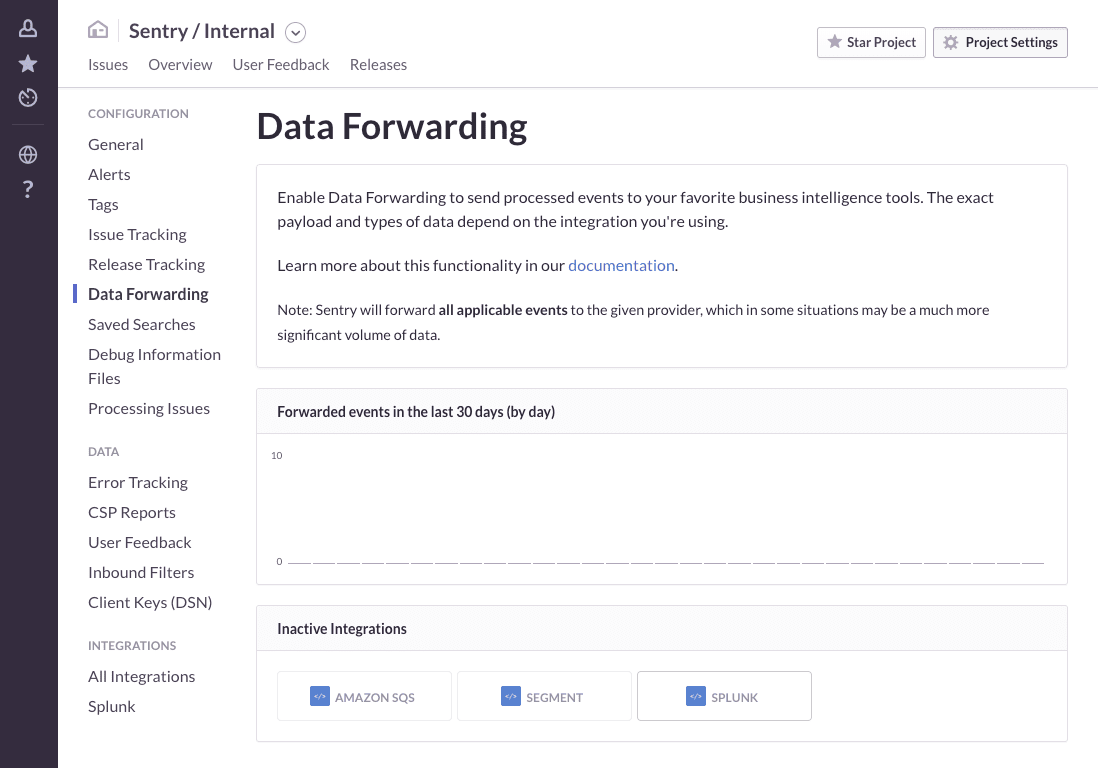
In Sentry, navigate to the project you want to forward events from, and click "Project Settings".
Configure data forwarding in [Project] > Settings > Data Forwarding, and provide the required information for the given integration.
After navigating to Data Forwarding, enable the Splunk integration:
Your instance URL is going to vary based on the type of Splunk service you’re using. If you’re using self-service Splunk Cloud, the instance URL will be the URL of the Splunk instance running the HTTP Event Collector (HEC):
https://<host>:8088
For all other Splunk Cloud plans, you’ll use the http-inputs prefix:
https://http-inputs-<host>:8088
If you’re using Splunk behind your firewall, you’ll need to fill in the appropriate host.
Once you’ve filled in the required fields, hit Save Changes:
We’ll now begin forwarding all new events into your Splunk instance.
Sentry will internally limit the maximum number of events sent to your Splunk instance to 1000 per second.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) or suggesting an update ("yeah, this would be better").