Okta SCIM Provisioning
Set up Okta's SCIM Integration for Member and Team Provisioning
This feature is only available if your organization is on a Business or Enterprise plan.
If you change your organization slug, you'll also need to update it in the "Auth" section of your "Organization Settings" in Sentry.
- Create users
- Deactivate users
- Push groups
- Import groups
- Configure organization-level roles
- Update user attributes (organization-level roles only)
Okta SCIM provisioning requires:
- A subscription to Sentry Business Plan or higher.
- Configuration of SAML SSO for Okta as documented here, or use the Okta sign-on tab in your Sentry Okta application to configure SAML.
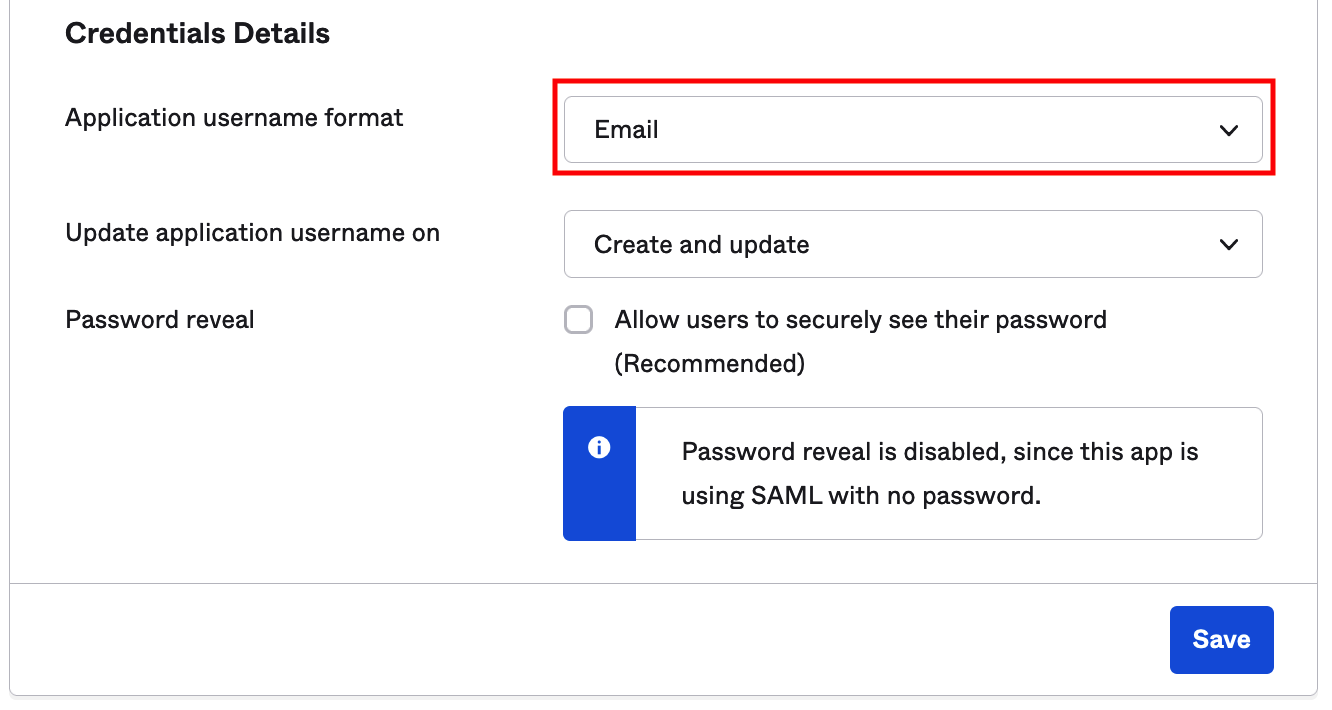
- Selection of Email for the Application username format in the Sign On application tab in Okta.
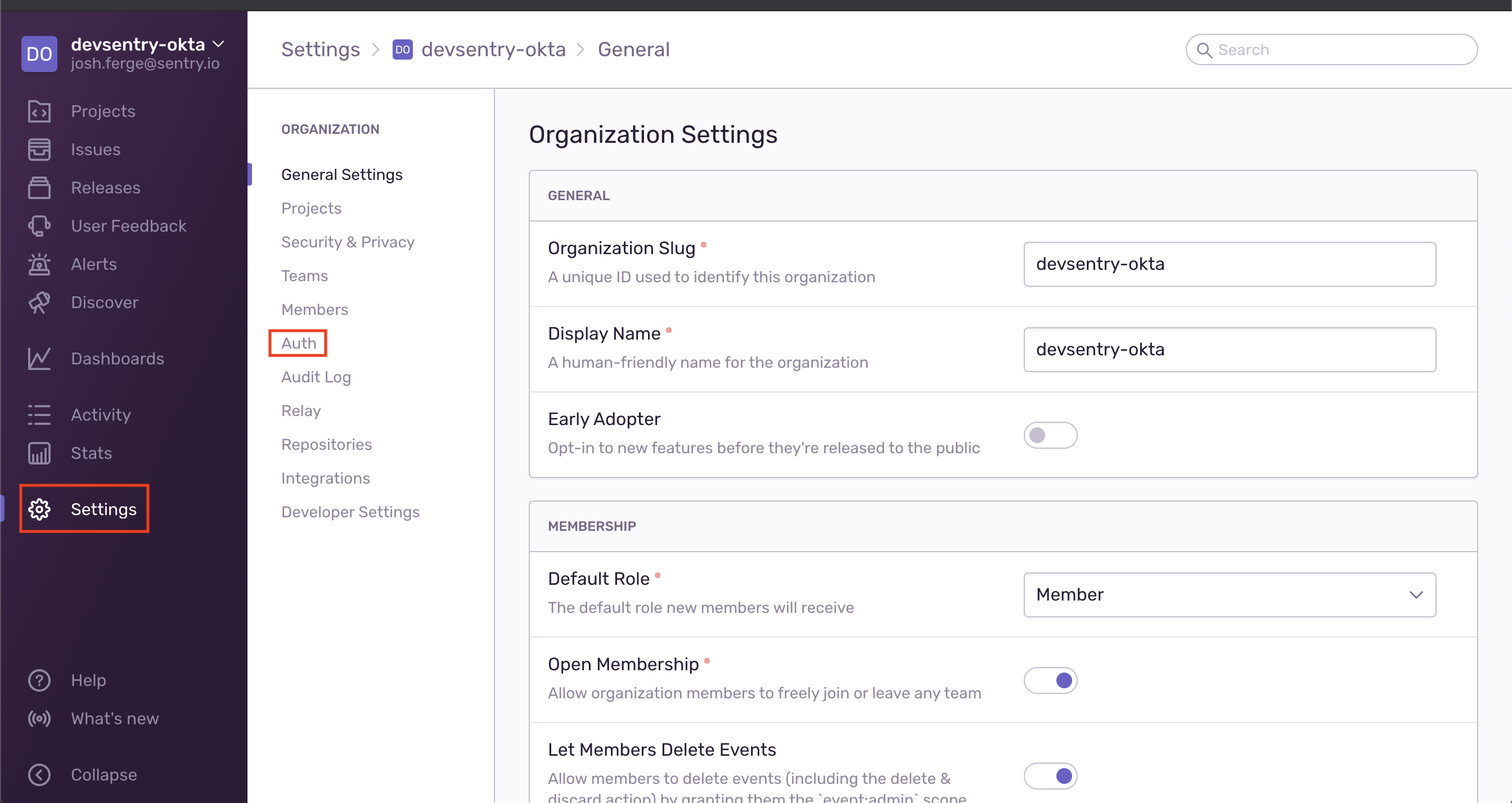
- Sign in to sentry.io. Select Settings > Auth
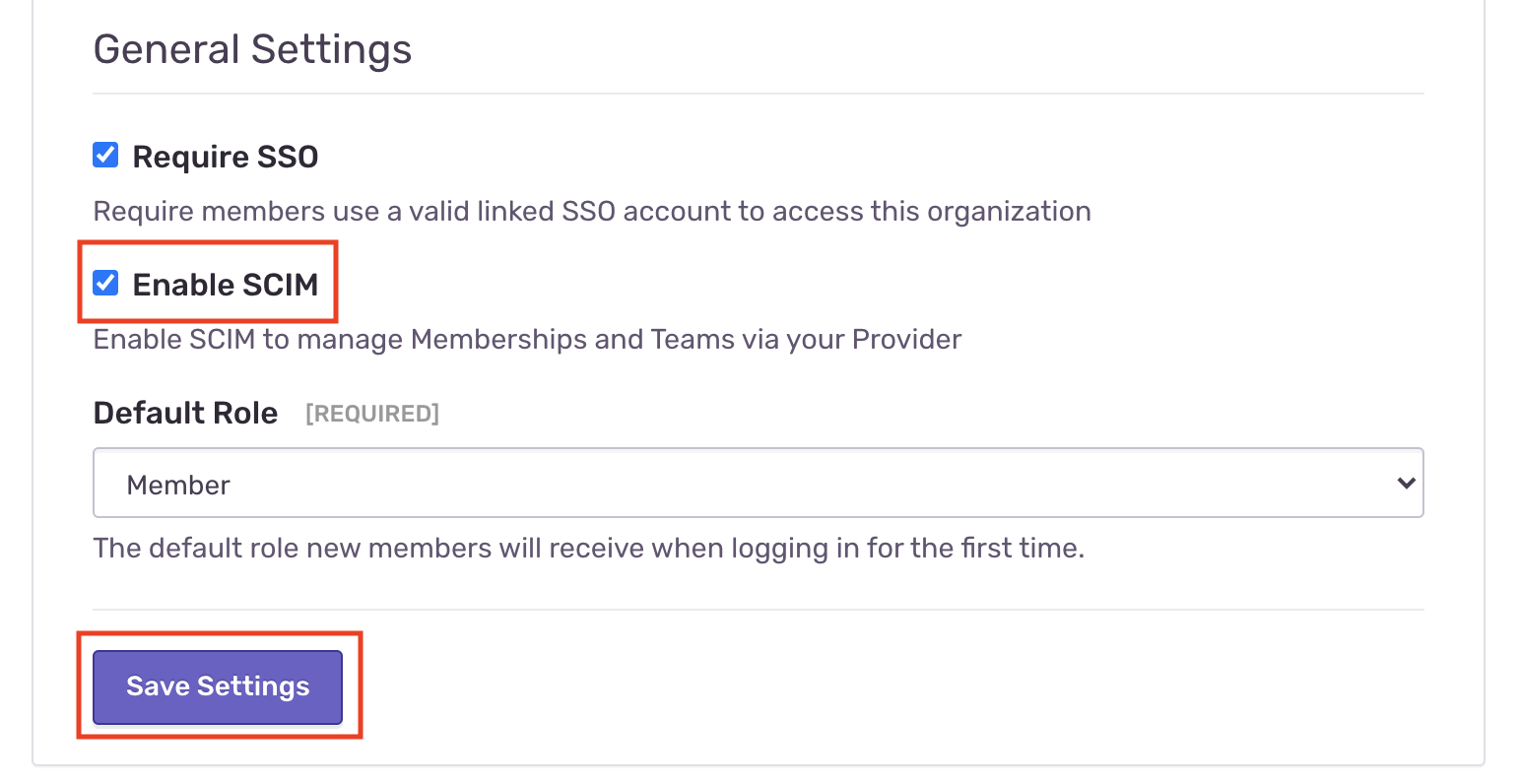
- Under General Settings select "Enable SCIM", then "Save Settings"
 Sentry will display "SCIM Information" that contains your Auth Token and SCIM Base URL.
Sentry will display "SCIM Information" that contains your Auth Token and SCIM Base URL. 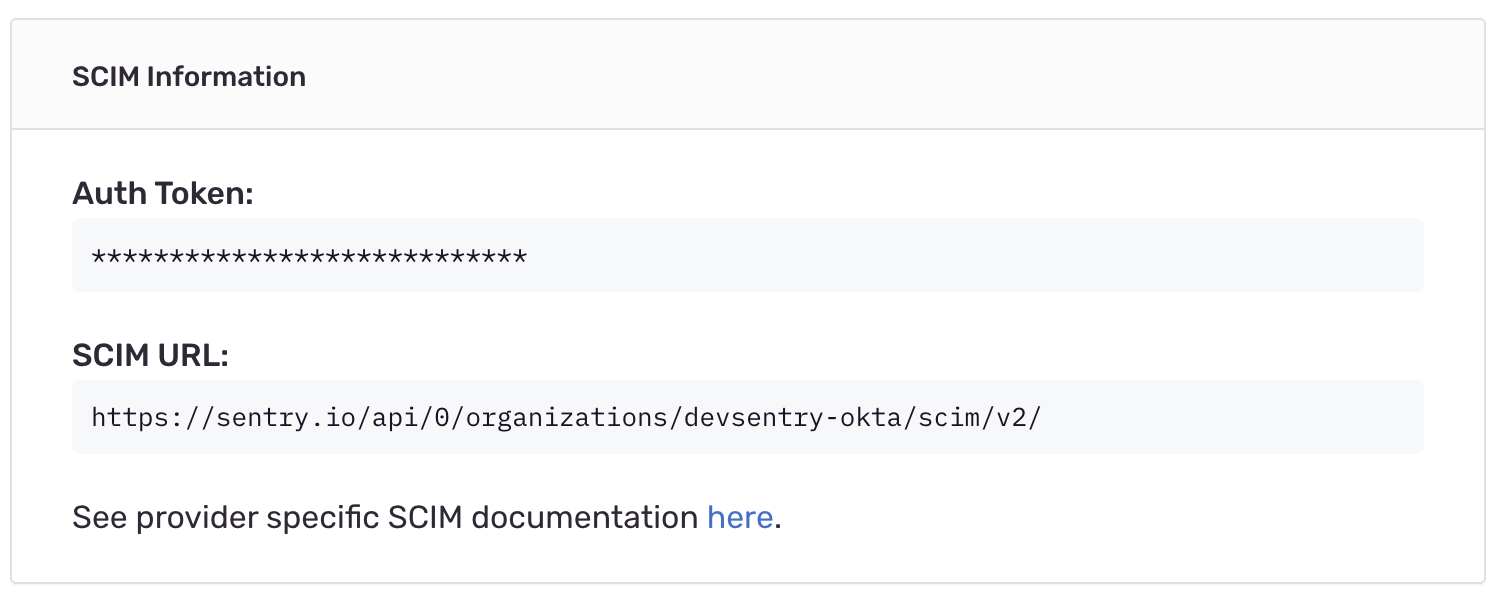
Sign in to your Okta organization with your administrator account. From the admin console's sidebar, select Applications > Applications, then select the existing Sentry application.
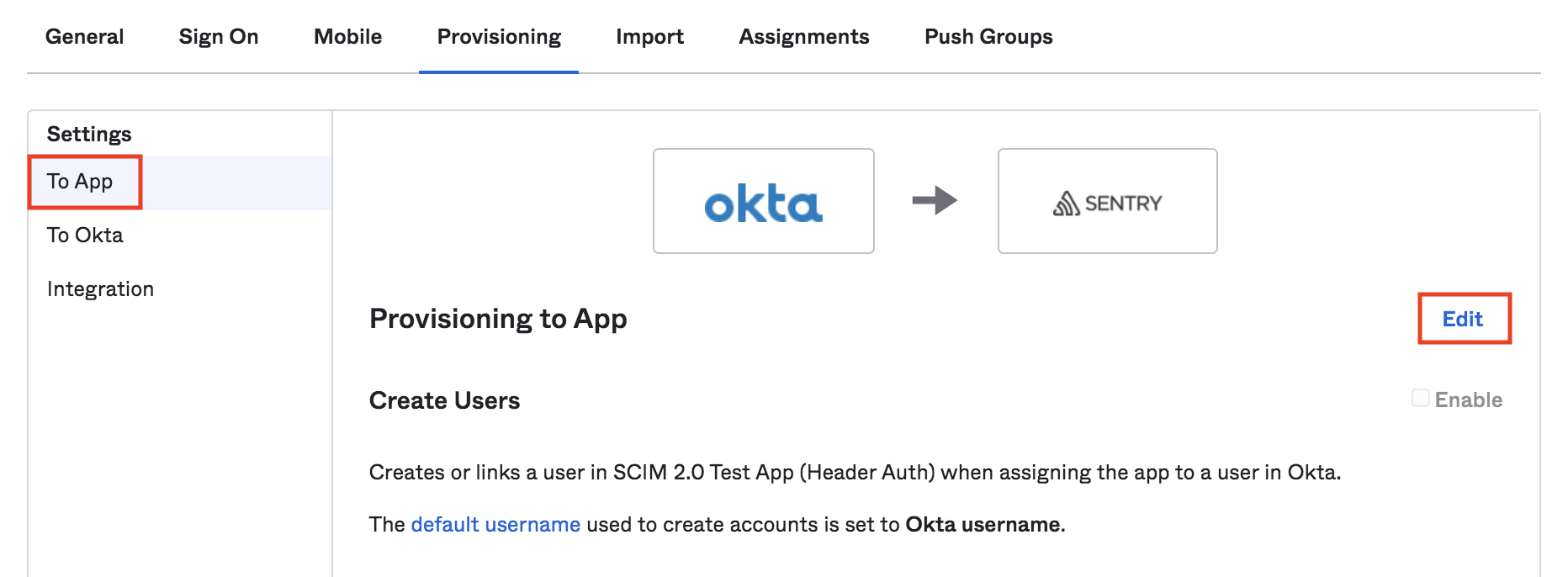
Select the "Provisioning" tab, then "Configure API integration".
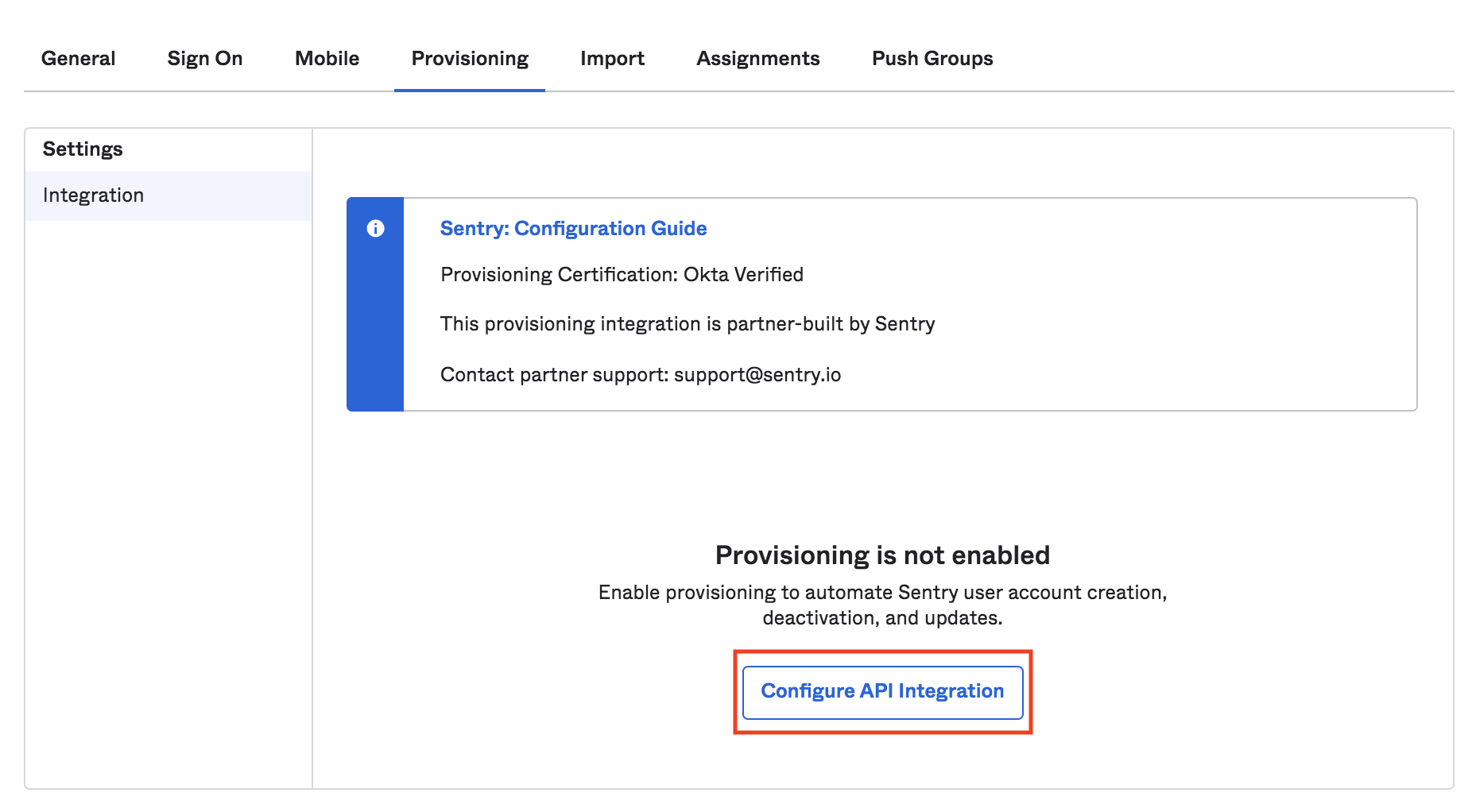
Select "Enable API Integration", then enter the SCIM URL from the auth settings page as the Base URL field.
For the API Token, copy the Auth Token value from the auth settings page.
Select "Test API Credentials". You should see a "the app was verified successfully" message appear.
Select "Save" to be directed to SCIM App settings.
Enable both "Create Users" and "Deactivate Users", then click the "Save" button.
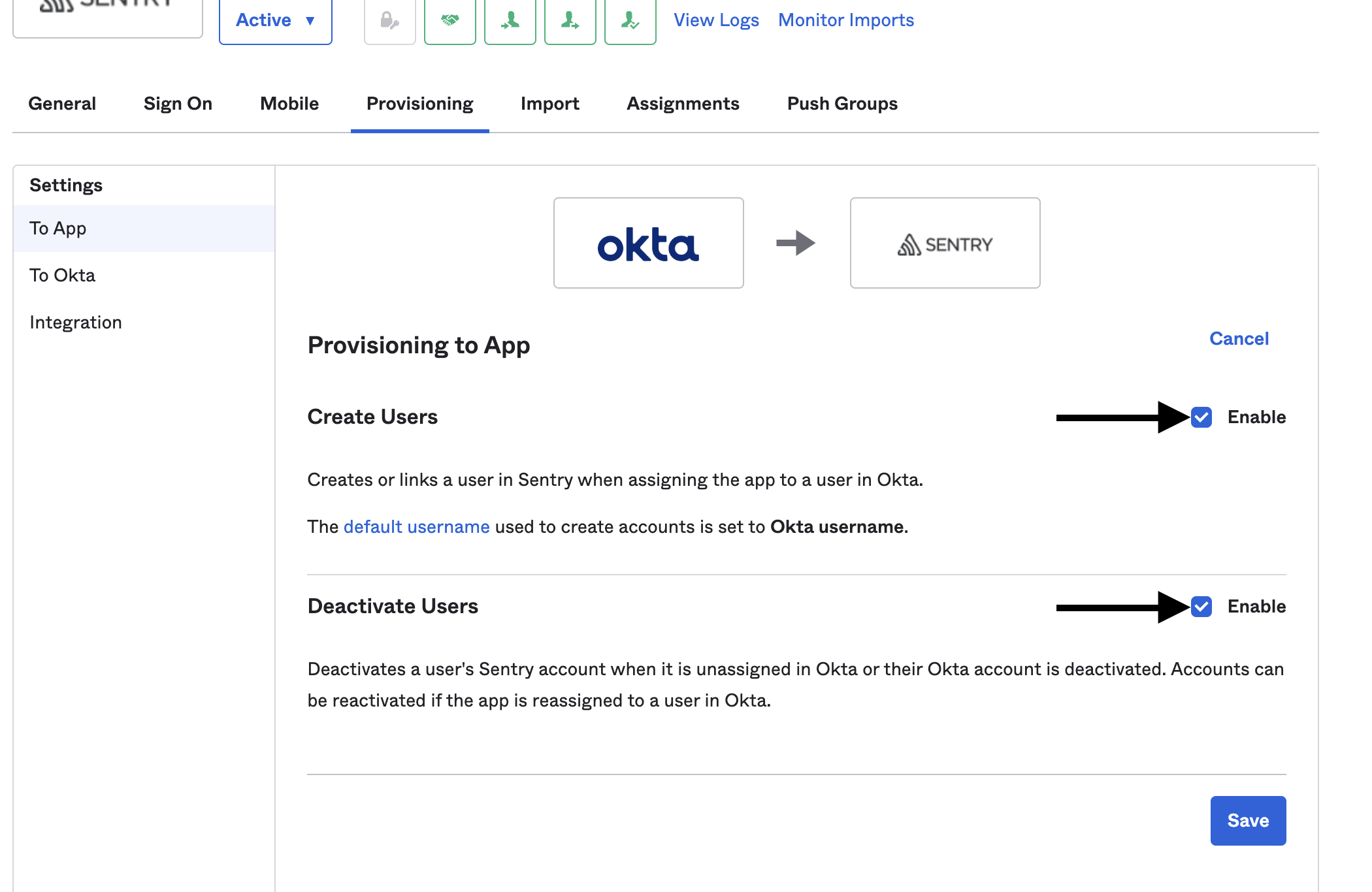
Once these changes have been made, newly assigned users will be sent an invitation email. If a user gets un-assigned, they'll be removed from their organization in Sentry.
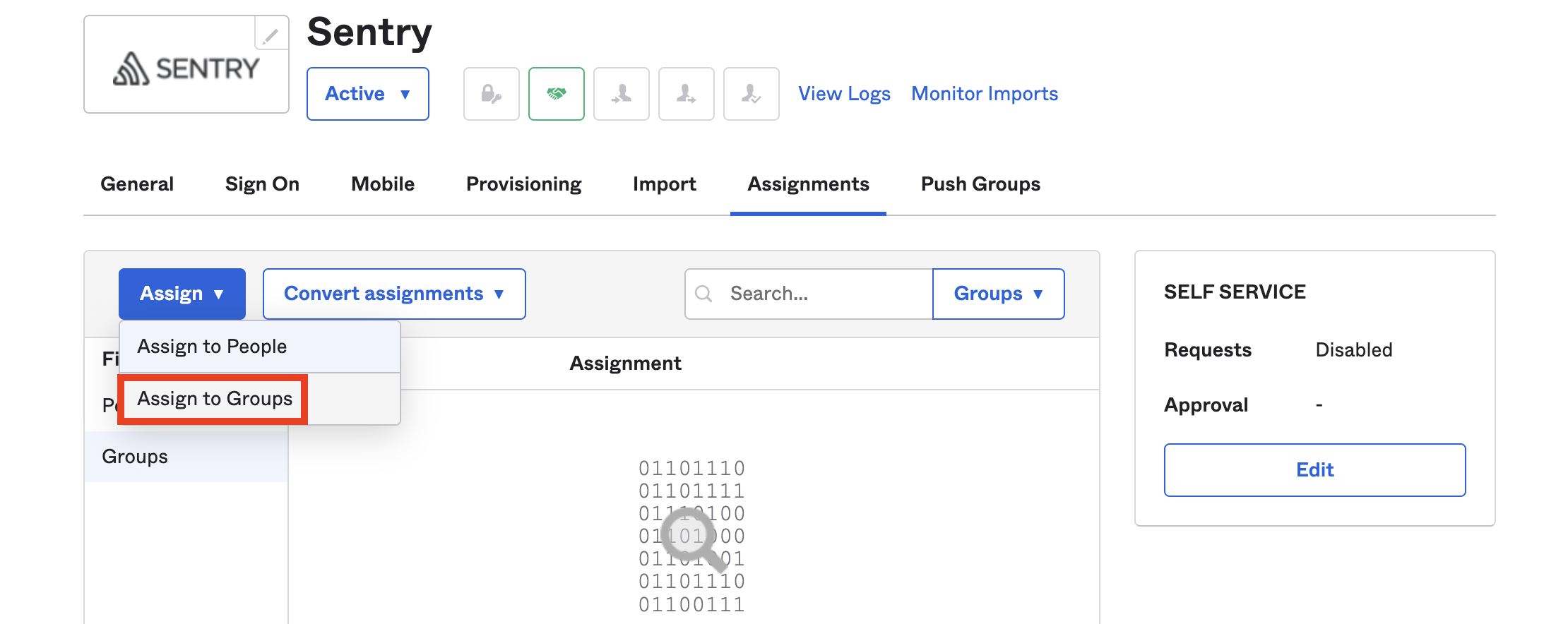
You can use "Push Groups" to sync and assign groups in Okta; they'll be mirrored in Sentry teams.
If you use Okta to assign organization membership, you’ll be unable to make membership changes through Sentry and will need to continue using Okta. To remove these users, deprovision them in Okta.
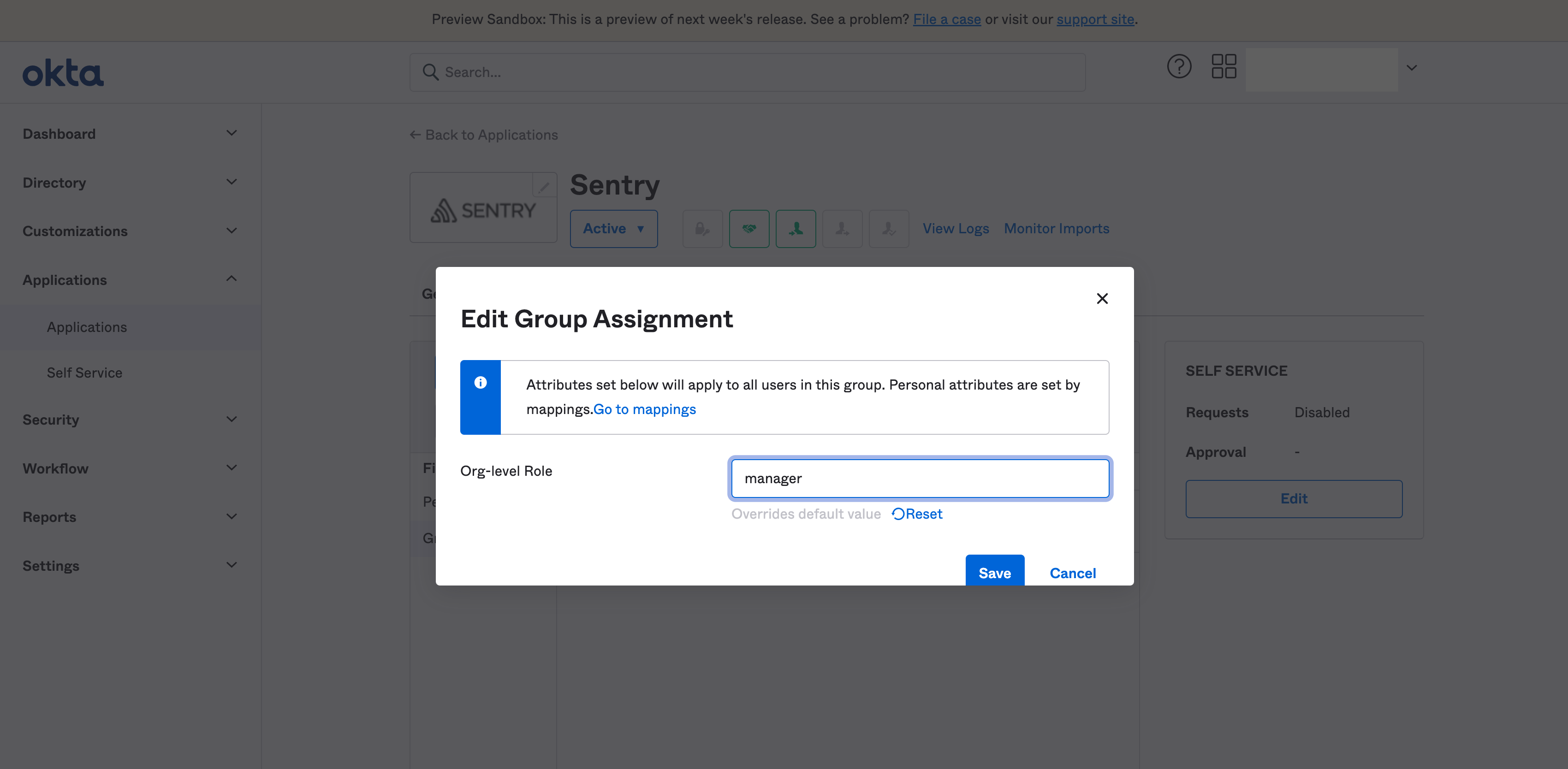
Here's how to assign an organization-level role to an Okta group:
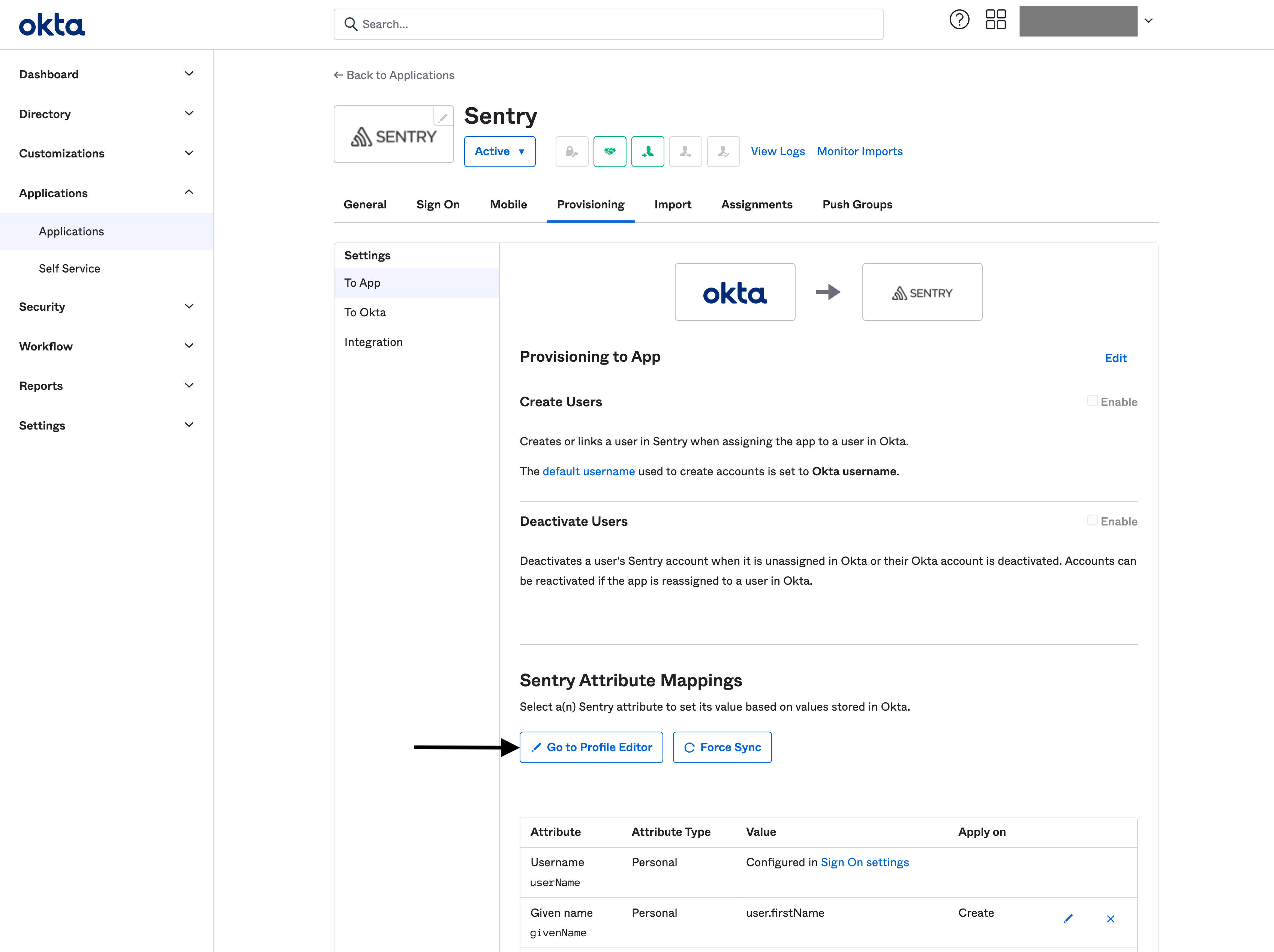
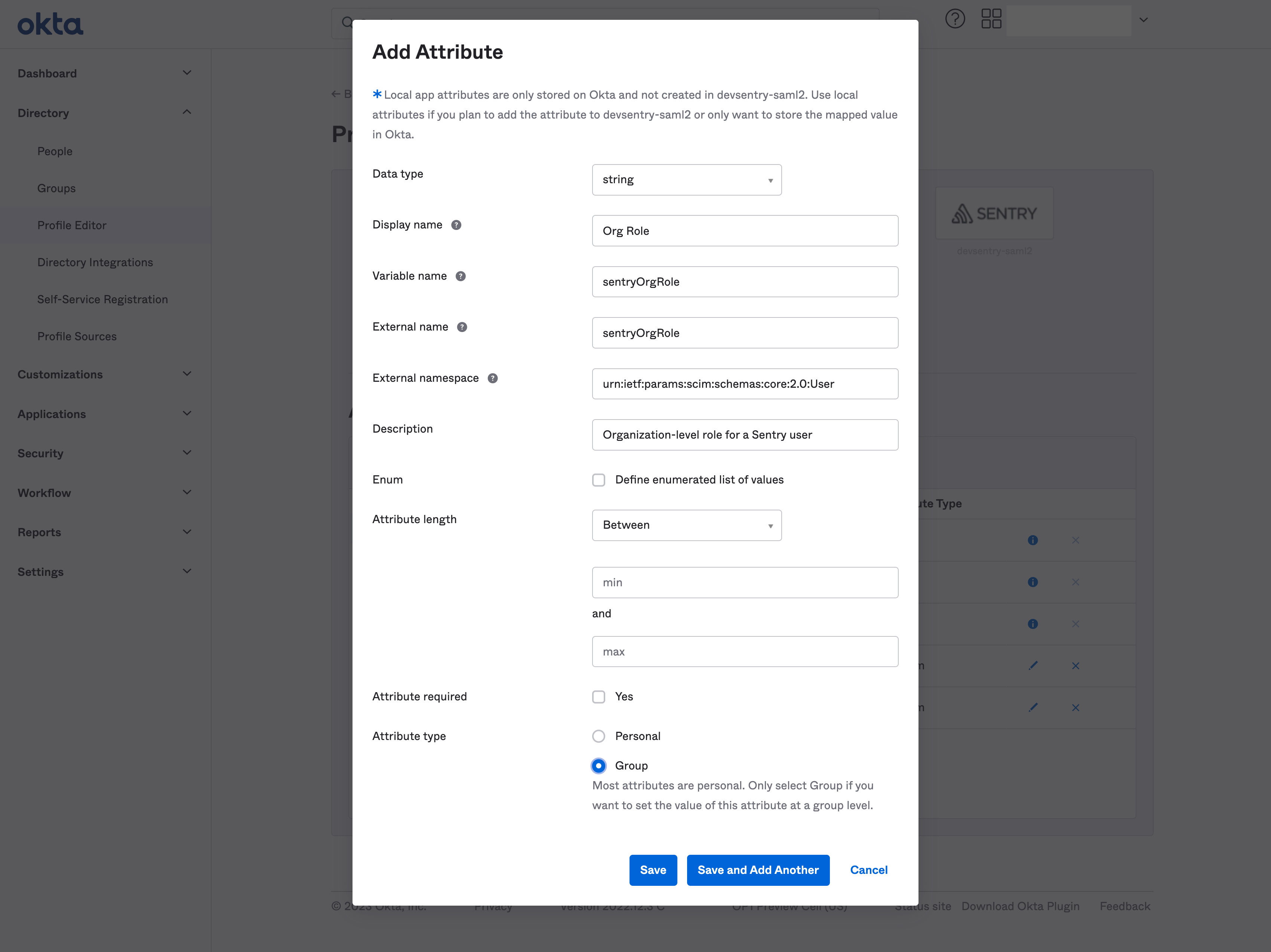
Add a new custom attribute to your Okta application profile
Navigate to your application settings in Okta
Fill out the form with the following settings (You can set whatever value you want for any setting not listed below.):
- Data Type:
string - Display Name:
Org Role - Variable Name:
sentryOrgRole - External name:
sentryOrgRole - External namespace:
urn:ietf:params:scim:schemas:core:2.0:User - Attribute type:
Group
- Data Type:
- If the
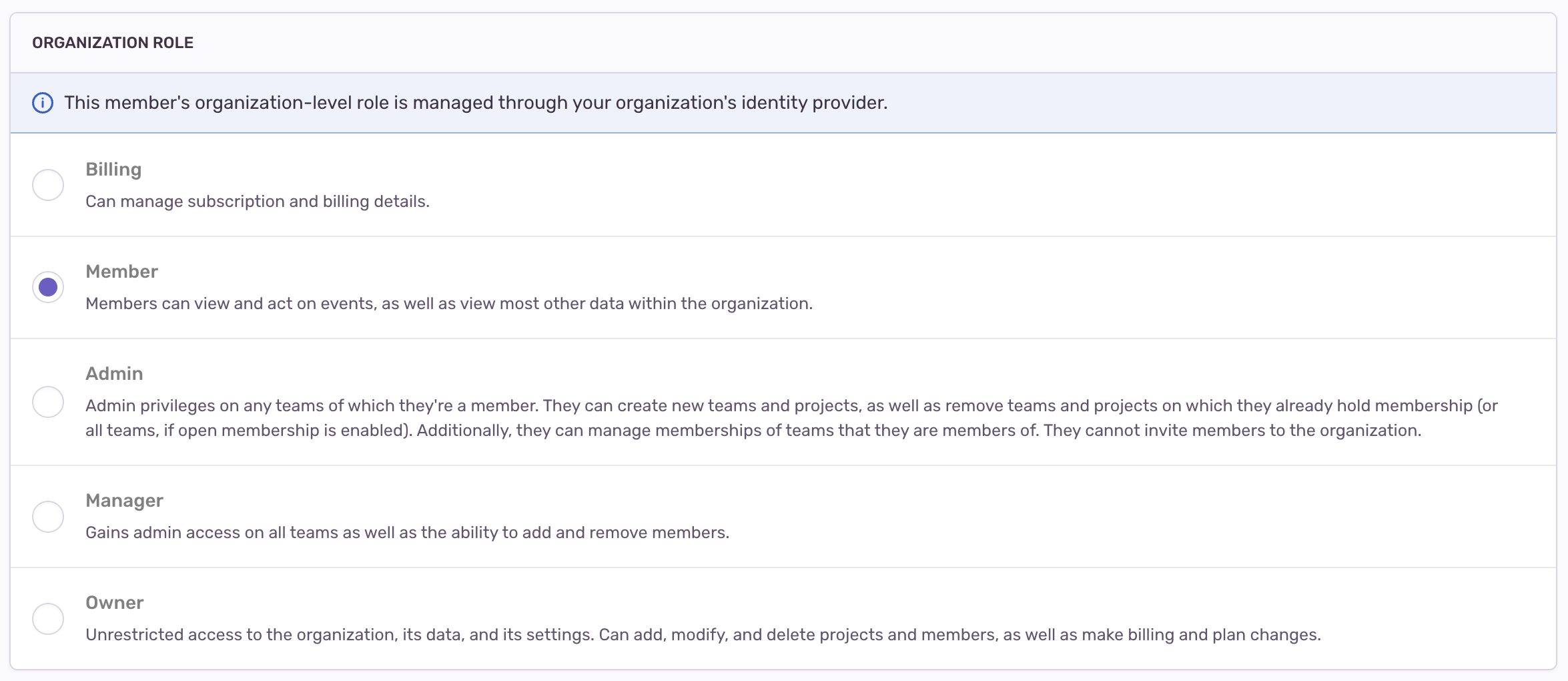
sentryOrgFieldfield is left blank, group members will be provisioned with the default organization-level role. This default role can be configured in Sentry, under Settings -> Organization -> Auth. Otherwise, the role must be one of the following:- Admin
- Manager
- Billing
- Member
- Invalid role names will prevent group members from being provisioned. To try again, you'll need to remove the group first.
- For security reasons, the "Owner" role cannot be provisioned through SCIM. However, you can deprovision users who have the "Owner" role in Sentry, but aren't provisioned through SCIM.
- For self-hosted users with custom roles, this extends to any role with the
org:adminpermission
- For self-hosted users with custom roles, this extends to any role with the
If a user is a member of multiple Okta groups, only the attributes set by the first group will be used.
If you use Okta to assign organization-level roles, you’ll be unable to make membership changes through Sentry and will need to continue using Okta. To change a user's organization-level role, you will need to deprovision and then reprovision them with the new role.
Users who've had their roles assigned via Okta will only be able to make membership changes via Okta.
Currently, Sentry only supports the ability to update user attributes for organization-level roles. You'll be able to edit the attribute for users assigned to your application once you've added the sentryOrgRole attribute to your Okta application profile.
The user's role in Sentry will reflect their organization role in your Auth settings. This means that if you change a user's attribute to blank, their organization-level role will be removed from Sentry.
Make sure that Create User and Deactivate User are enabled in the "Provisioning" tab of your Sentry application in Okta (see Okta Configuration step 7).
Assigning Sentry to a group in Okta is the same as assigning Sentry to every member of that group. Functionally, this provisions every group member within Sentry, but doesn't create a team. To create a team, push the group to Sentry from the Push Groups tab of your Sentry application in Okta.
Pushing a group via Okta tells Sentry to create a new team with the same name as the Okta group. Only those users who've already been provisioned as members of that group will be added to the Sentry team. Make sure that your group in Okta contains the appropriate users and that they've already been provisioned.
If possible, isolate the user(s) that are causing the error. Then remove the user(s) from Sentry and provision them again with Okta.
When team membership is managed by an identity provider (such as Okta), it can only be updated or revoked via that identity provider.
If you use Okta to assign members to a team, you’ll be unable to make membership changes through Sentry and will need to continue using Okta.
Make sure that Deactivate User is enabled in the "Provisioning" tab of your Sentry application in Okta. Re-provision the user, then remove them again.
Change the user's role attribute to blank.
- The Import Users feature isn't currently supported because Sentry's SCIM API doesn't support the user
nameattribute fields:firstNameandlastNameat this time. For compatibility purposes, they're returned asN/Avalues. - If the
activefield is set tofalsefor any given user, their organization member record gets deleted. - The only filter operation supported for resources is
eq. - When provisioning a new team, Sentry will both normalize and convert the team
displayNameuppercase to lowercase, and convert spaces to dashes. - The GET /Groups endpoint cannot return more than 10000 members in a group, see SCIM API documentation for more information.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) or suggesting an update ("yeah, this would be better").